
Keeping the organization safe from advanced threats sounds like a challenging task because it is. One of the key requirements is to quickly and efficiently detect malware, both known and unknown. As there is no single technology that can provide adequate protection, the recommended practice is to implement a tightly integrated, multi-layered approach where malware, should it escape one security control, is caught by the next.
A best-of-breed sandbox is therefore an essential component of a robust, multi-layered, comprehensive cyber protection strategy. Hence, Malware Sandboxing needs to be an integral part of your Advanced Threat Protection strategy.
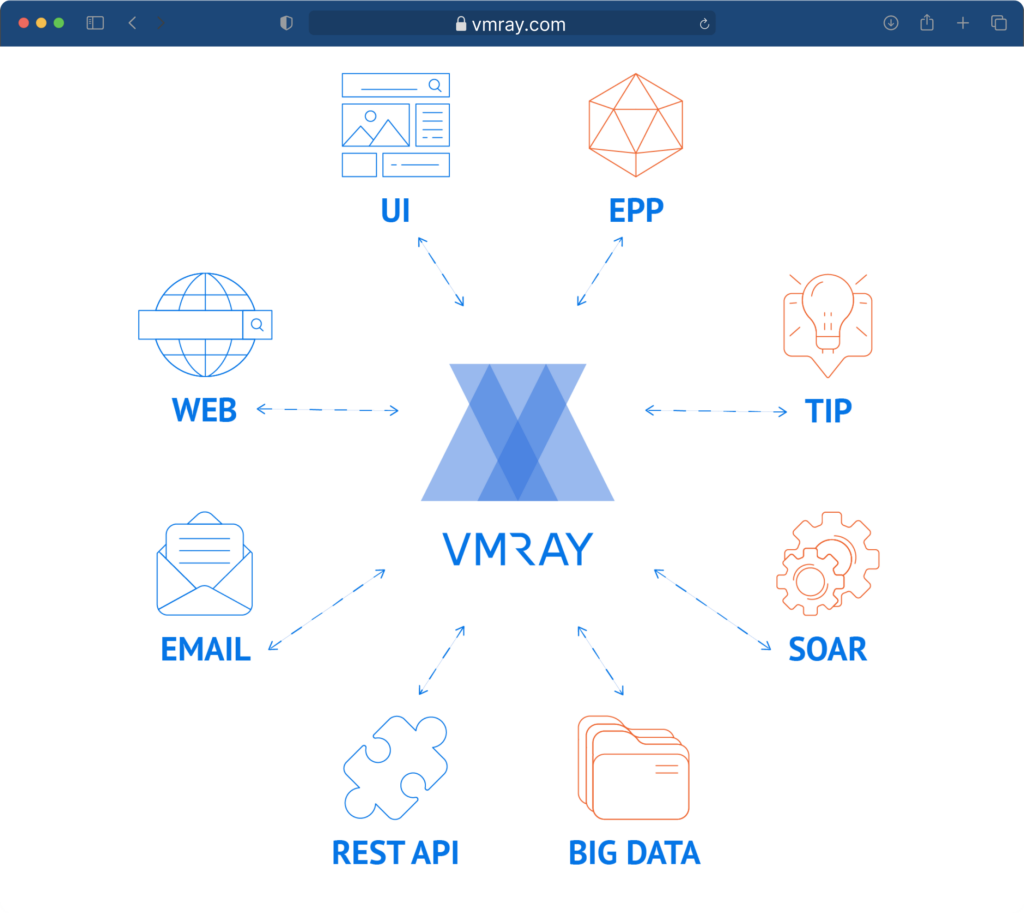
VMRay Platform involves a ground-breaking sandbox, and 30+ best-of-breed technologies that bring additional capabilities to detect the threats that others miss.
Keeping the organization safe from advanced threats sounds like a challenging task because it is. One of the key requirements is to quickly and efficiently detect malware, both known and unknown. As there is no single technology that can provide adequate protection, the recommended practice is to implement a tightly integrated, multi-layered approach where malware, should it escape one security control, is caught by the next.
Keeping the organization safe from advanced threats sounds like a challenging task because it is. One of the key requirements is to quickly and efficiently detect malware, both known and unknown. As there is no single technology that can provide adequate protection, the recommended practice is to implement a tightly integrated, multi-layered approach where malware, should it escape one security control, is caught by the next.
To provide true business benefit, a sandbox must go beyond mere malware analysis and add value to the extended environment.
VMRay Analyzer helps you to design a security approach that leverages integration, automation, and shared threat intelligence. With VMRay Analyzer you can achieve:
Connected and automated workflows are the secret of a successful SOC. That is why a best-of-breed sandbox with strong process automation capabilities is an essential building block for SOC efficiency when staff resources are stretched thin, and teams are flooded with alerts from different sources. The right sandbox will be able to positively impact the most important SOC metrics, such as Time-to-Detection, Time-to-Qualify, Time-to-Triage, Time-to-Investigate, and Time-to-Respond.
VMRay Platform involves a best-of-breed sandbox as well as 30+ unique detection and analysis technologies. It empowers efficiency by supporting alert ingress from a large range of disparate sources. our platform also enables automating every stage of the malware and phishing detection & analysis process, and provides the information needed to confidently validate and triage alerts by the level of severity.
Not surprisingly, advanced malware sandboxing is a foundational tool for incident response and threat hunting. Both are human-centric activities and rely on detailed insights into malware behavior, meaningful context and noise-free data to correlate events and connect the dots.
VMRay’s accurate, in-depth, noise-free reporting starts with the comprehensive data gathered during threat analysis. VMRay captures and categorizes every interaction between the malicious files and URLs and the analysis environment, down to the granular level of function logs. The reports present only the relevant information for understanding the threat behavior being analyzed – extraneous information is filtered out.
Security teams routinely invest in third-party threat intelligence services to provide external insights for automated malware detection, incident response, threat hunting, and vulnerability management. However, most security teams struggle to generate in-house threat intelligence that is based on unique attacks that they are currently seeing inside their networks: data that is not available from third parties.
With VMRay Analyzer, analysts can automatically extract highly reliable Indicators of Compromise (IOCs) from data gathered during threat analysis, creating actionable threat intelligence to enrich their third-party data. Cybersecurity blog
It has always been good advice to make the most of existing investments. This also applies to investments in security solutions. If organizations want to strengthen their defenses against advanced threats, they should first look for ways to increase the efficacy of the security stack they already have in place.
VMRay Analyzer and VMRay Email Threat Defender enhances the investments organizations have made in the security ecosystem. These include web and Email Security solutions, EDR, SOAR, SIEM, Threat Intelligence and other tools. VMRay Platform helps the organization to adopt a security approach that is based on integration, automation, and shared threat intelligence.
Contact our security experts for a personalized demo call and arrange a free trial to evaluate VMRay Analyzer.
Check our latest insights on malware, phishing, sandboxing, AI in cybersecurity, and much more.
Browse the courses about alert handling, deep threat analysis and response, threat intelligence generation and more.
See real-world examples of VMRay’s best-in-class malware analysis and detection platform.




