Global Top 10 Technology Company | Threat Intelligence Team





Supplement existing cyber threat intelligence repositories with targeted, specific threat information.
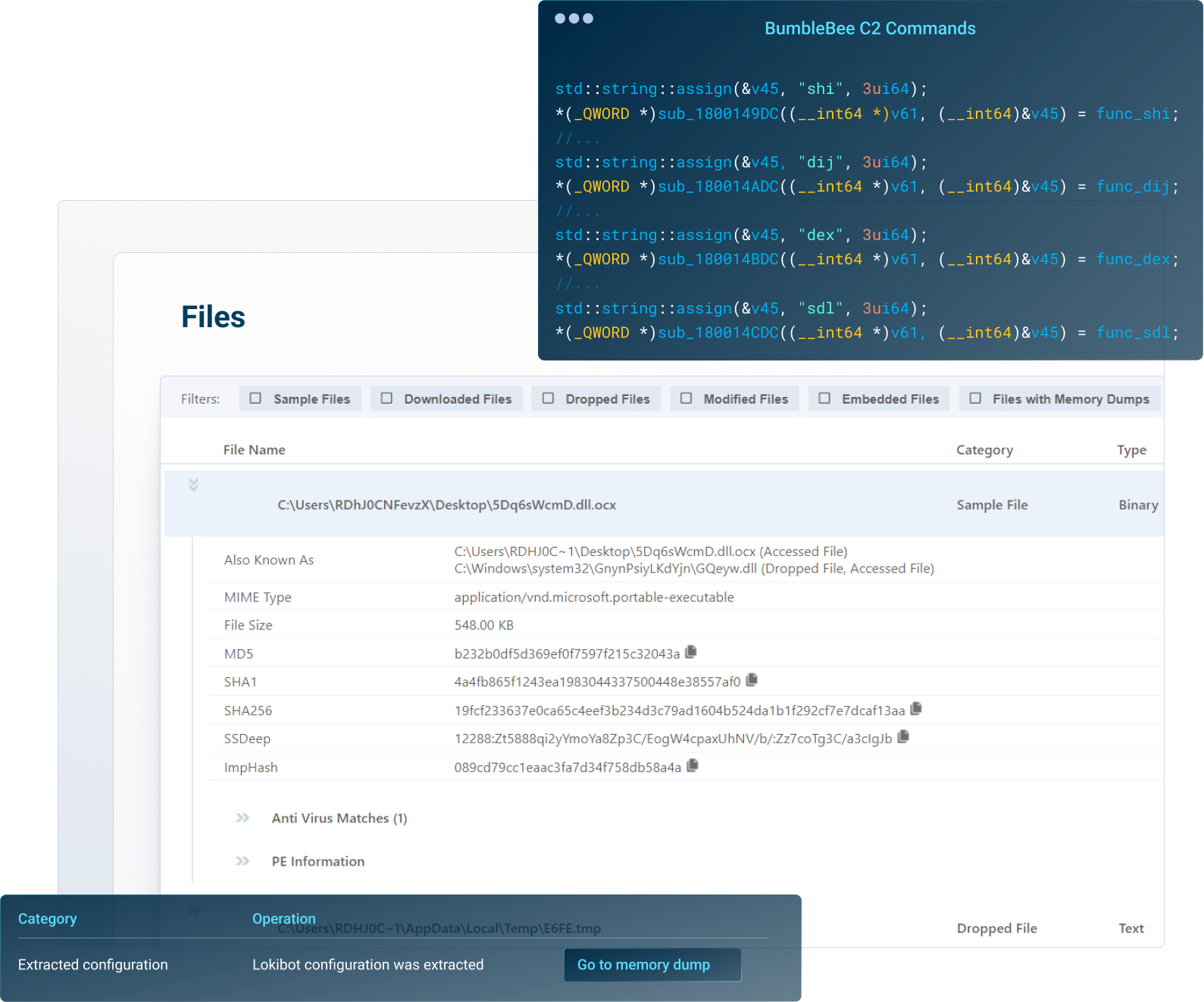
VMRay allows for the collection of threat intelligence by analyzing malware and phishing attacks down to the lowest level of code to extract noise free IOCs.
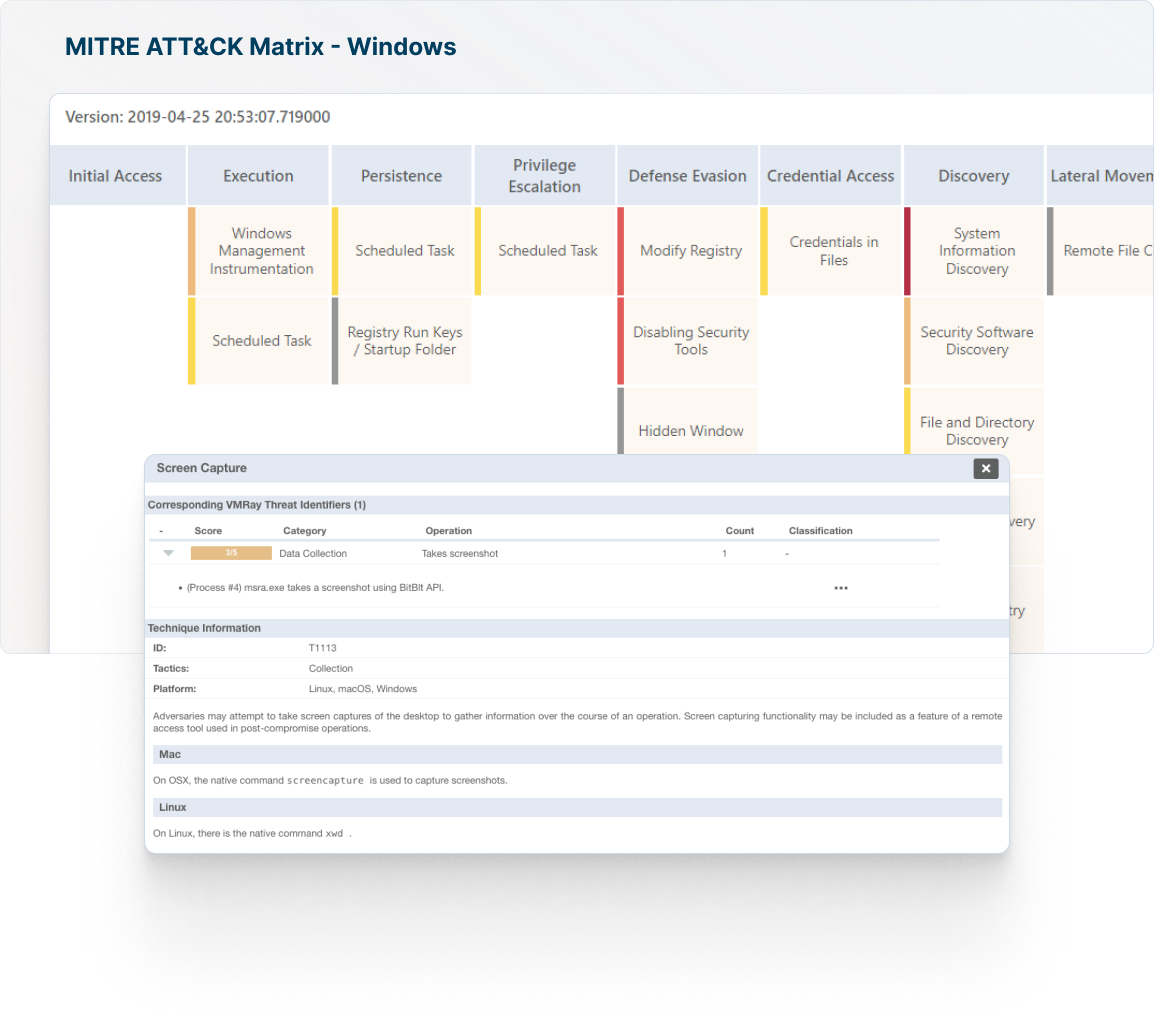
Enhance operational threat intelligence with MITRE ATT&CK mapping to identify potential attack vectors and threat actor TTPs.
IOCs can be used by Detection Engineering Teams to diminish any current or future threat that expose organizational risk before any mitigating vendor signatures become available.
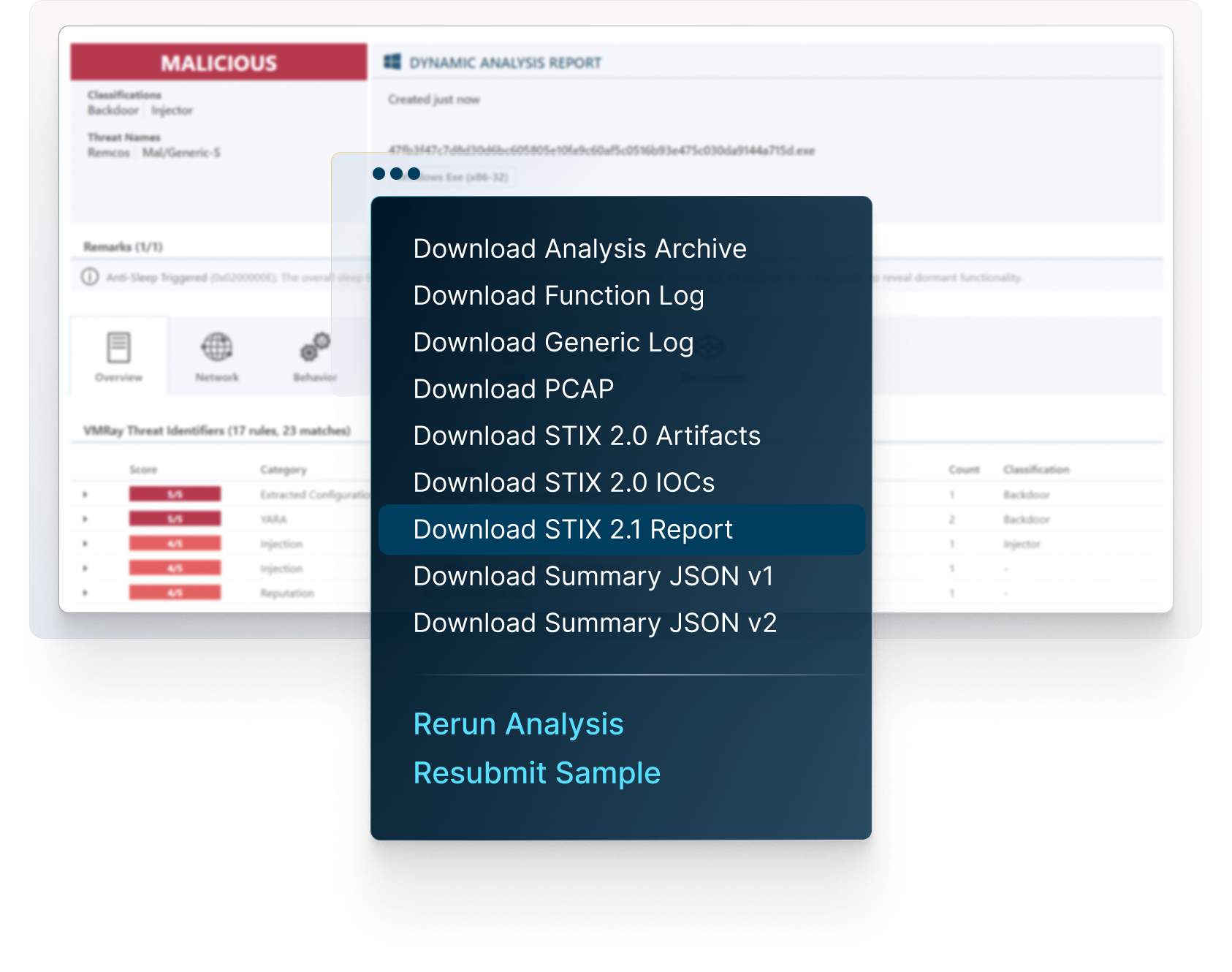
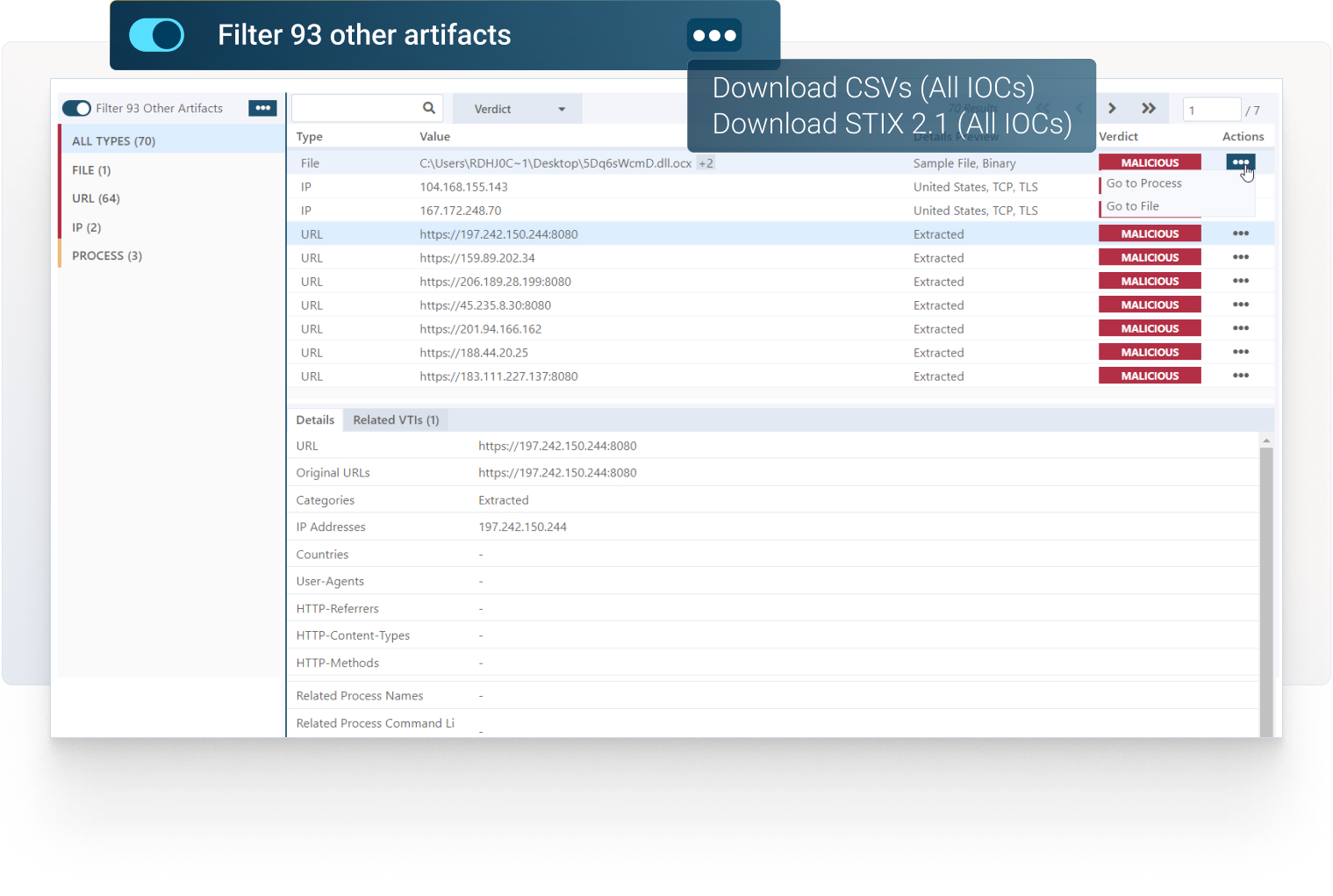
VMRay supports multiple formats for exporting IOCs to other security tools and threat repositories, including JSON, CSV and STIX 2.1.
Context to help understand an attack accurately.
Correlation of indicators from inside an environment with external threat intelligence data provides context to help understand the who, what, where, when, why, and how of an attack.




Access comprehensive reports, explore network connections, get insight into malicious behaviors, map threats to the MITRE ATT&CK Framework, download IOCs and artifacts, and much more.
VMRay unites reputation analysis, static analysis, next-generation sandboxing, and machine learning into one single platform. Using VMRay to identify malware and phishing threats provides uncurated tactical, operational, and strategic threat intelligence on known and previously unknown Zero-Day threats.
Supplementing existing threat intelligence repositories with target specific threat information, VMRay helps SOC teams gain valuable insights to anticipate new threats and become more proactive when deploying defenses and mitigating attacks.
No. VMRay’s sandbox technology allows organizations to curate their own threat intelligence with threat information specific to their own ecosystem. Organizations build their own threat intelligence because it allows them to better understand the threat landscape and the potential risks specifically targeting their company. This understanding can help Security Operations Center (SOC) teams to develop more effective security strategies, including better security policies, and improved incident response plans.
By sharing threat information and collaborating with external partners as well as other organizations in their industry, Governmental and commercial organizations can better identify and respond to targeted threats, potentially reducing the overall impact of cyber-attacks to better comply with regulatory requirements.
Typically, a malware or URL sample would require manual triage to identify if it was malicious or benign. Manual malware analysis is not scalable, even if the organization’s cybersecurity team has the necessary skills. Security teams require a more efficient approach to develop internal threat intelligence that can support their decisions and actions.
With VMRay’s sandbox technology, submitted samples are analyzed in minutes, not hours or days to provide the IOCs and artifacts necessary to identify compromised systems and mitigate threats. It accelerates incident response to speed investigations to resolution, while at the same time contributing to an overall reduction in MTTD and MTTR.
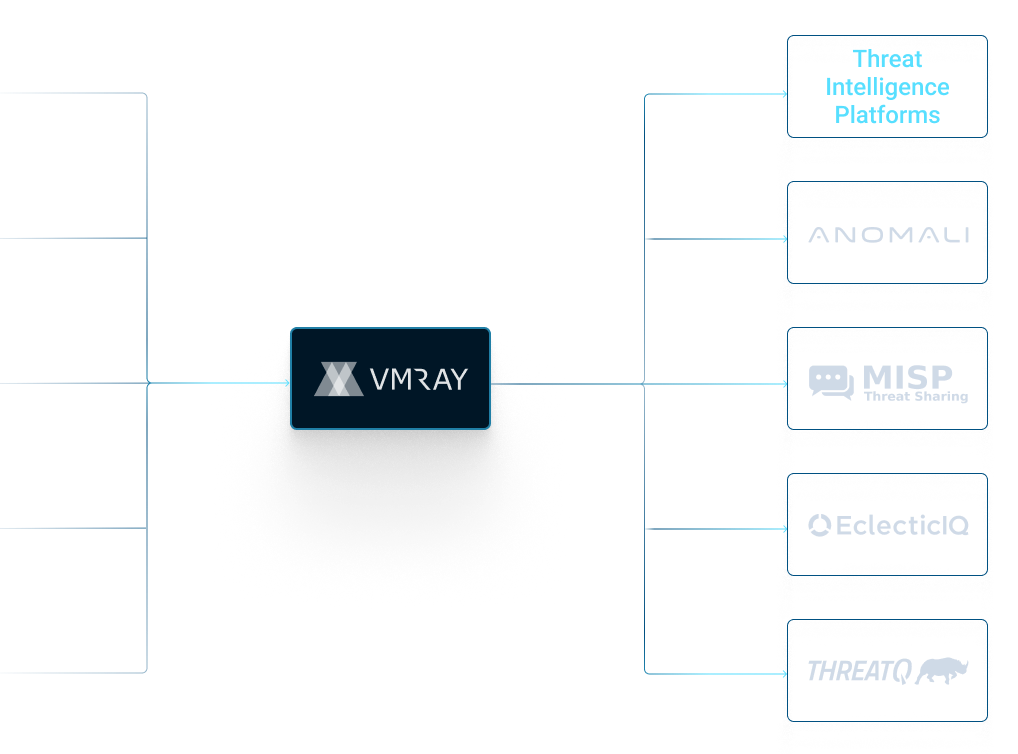
VMRay integrates with the following TIP platforms for threat intelligence extraction:
Anomali, Cyware, MISP, ThreatConnect, & ThreatQ.
VMRay’s value proposition goes beyond exceptional products, focusing on high-quality professional services and 24/7 customer support that eliminate skills gaps and drive success in dynamic cybersecurity environments to accelerate incident resolution.
Recognizing resource constraints faced by Security/IT teams, VMRay offers a comprehensive suite of services tailored for seamless onboarding, optimized configuration, and robust integrations – ensuring efficient deployment and maximizing solution efficacy.
VMRay addresses deployment concerns by offering a range of professional service offerings to get you up and running quickly. We leverage our expertise deploying hundreds of customers to ensure that you are up and running regardless of how complex your requirements may be.
X-press Onboarding
Our express onboarding service ensures a swift deployment while our expert team assists with configuration and provides guidance. Whether you’ve selected to utilize the VMRay Cloud or and on-premises solution, we will work with you to get the VMRay platform set up and configured to your requirements.
Automation Integration Deployment
Seamlessly integrate our solutions with your existing tools to enhance incident automation and strengthen your cybersecurity infrastructure. If your needs include taking advantage of the time and labor savings of integrating VMRay into your security ecosystem, we will work with you to configure our range of connectors to 3rd party platforms to other solutions within your environment.
Bespoke Training
Empower your team with tailored training options, including video recordings, accessible PDF materials, and in-person sessions. Basic training is provided during the on-boarding process and a variety of free training resources, both documentation and videos. Sometime customers want a more customized training solution to better align with their incident response plans. We will work with you to understand your specific requirements and deliver customized instructor based live training tailored to your specific needs.




