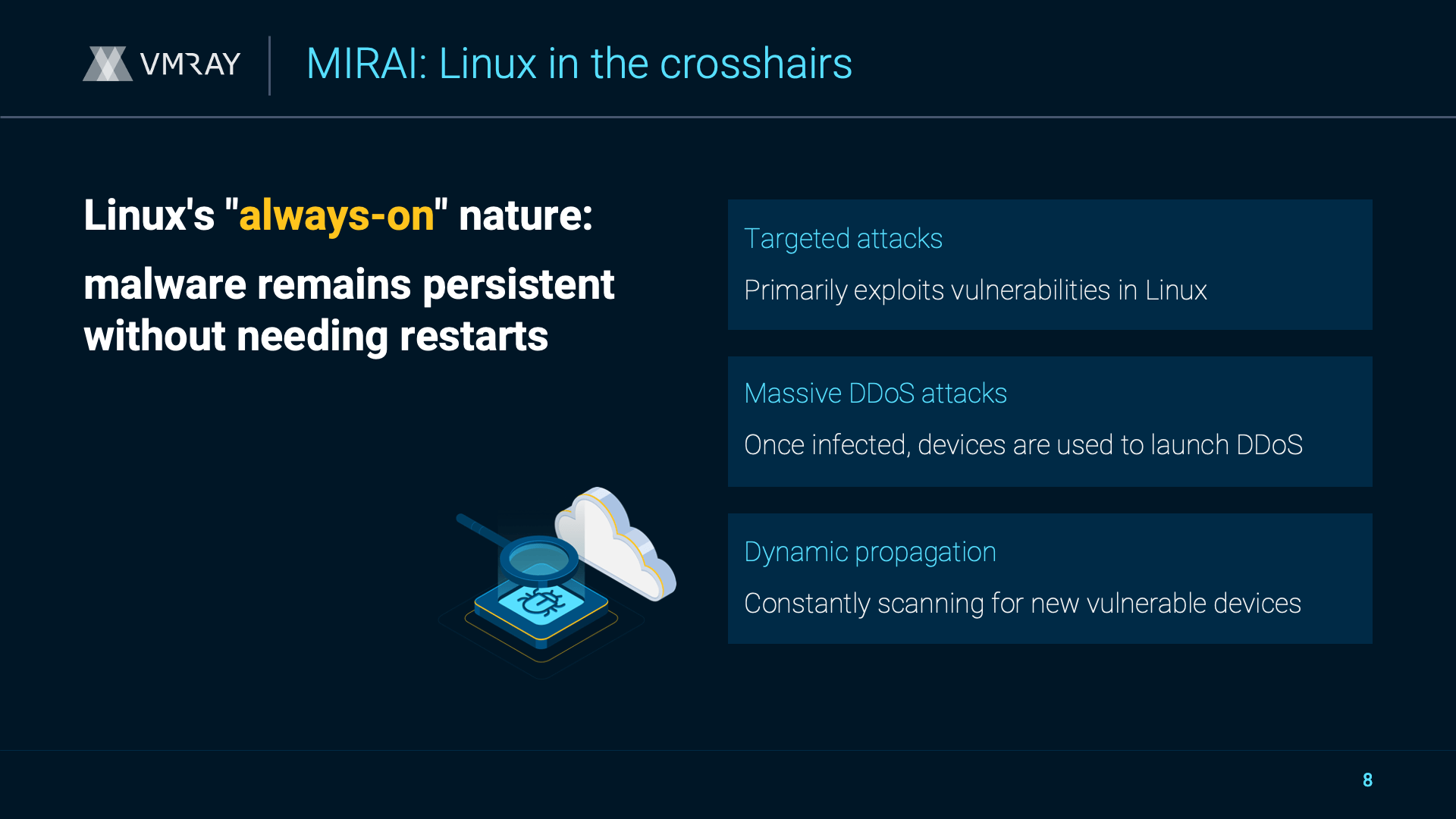
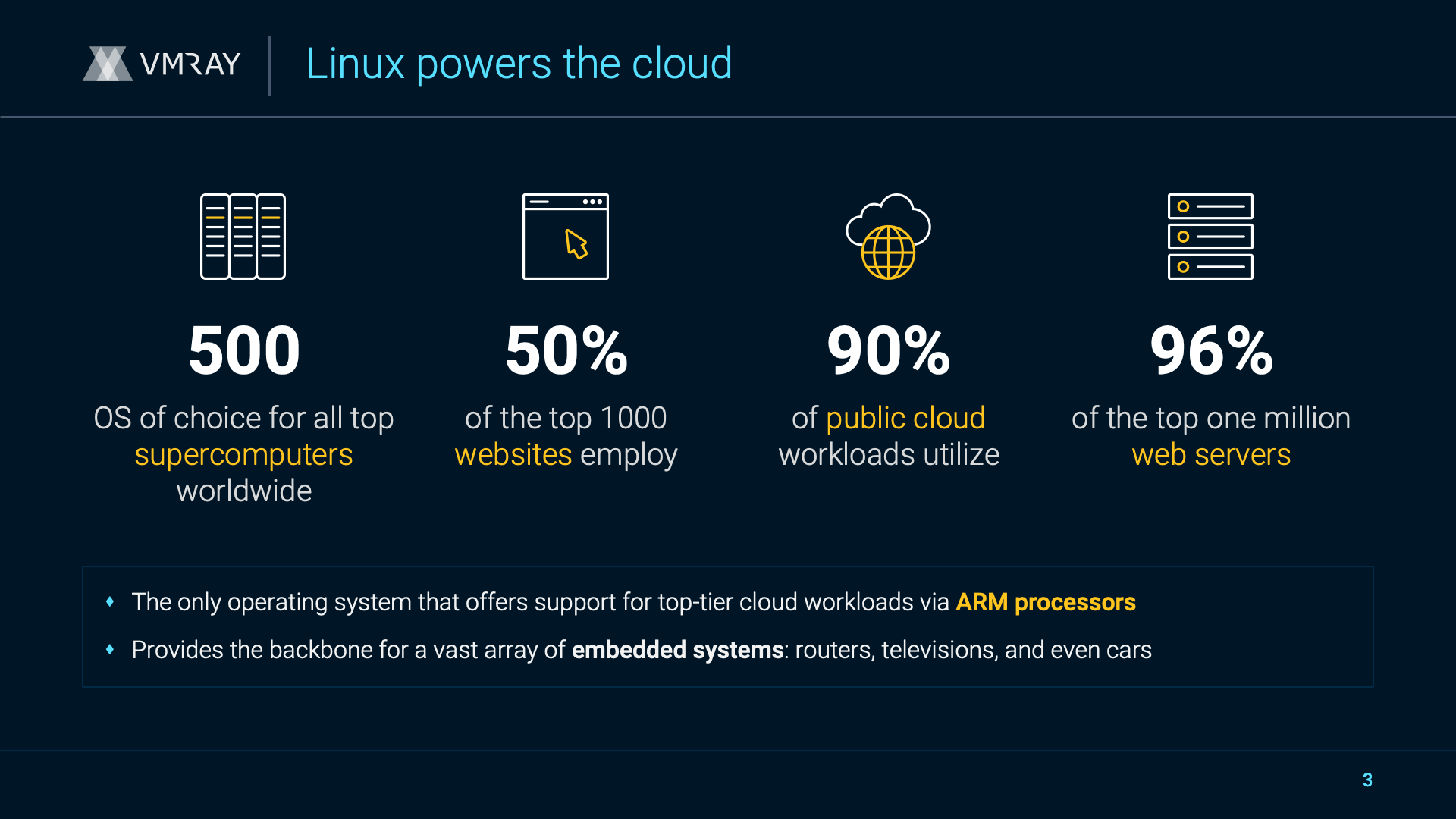
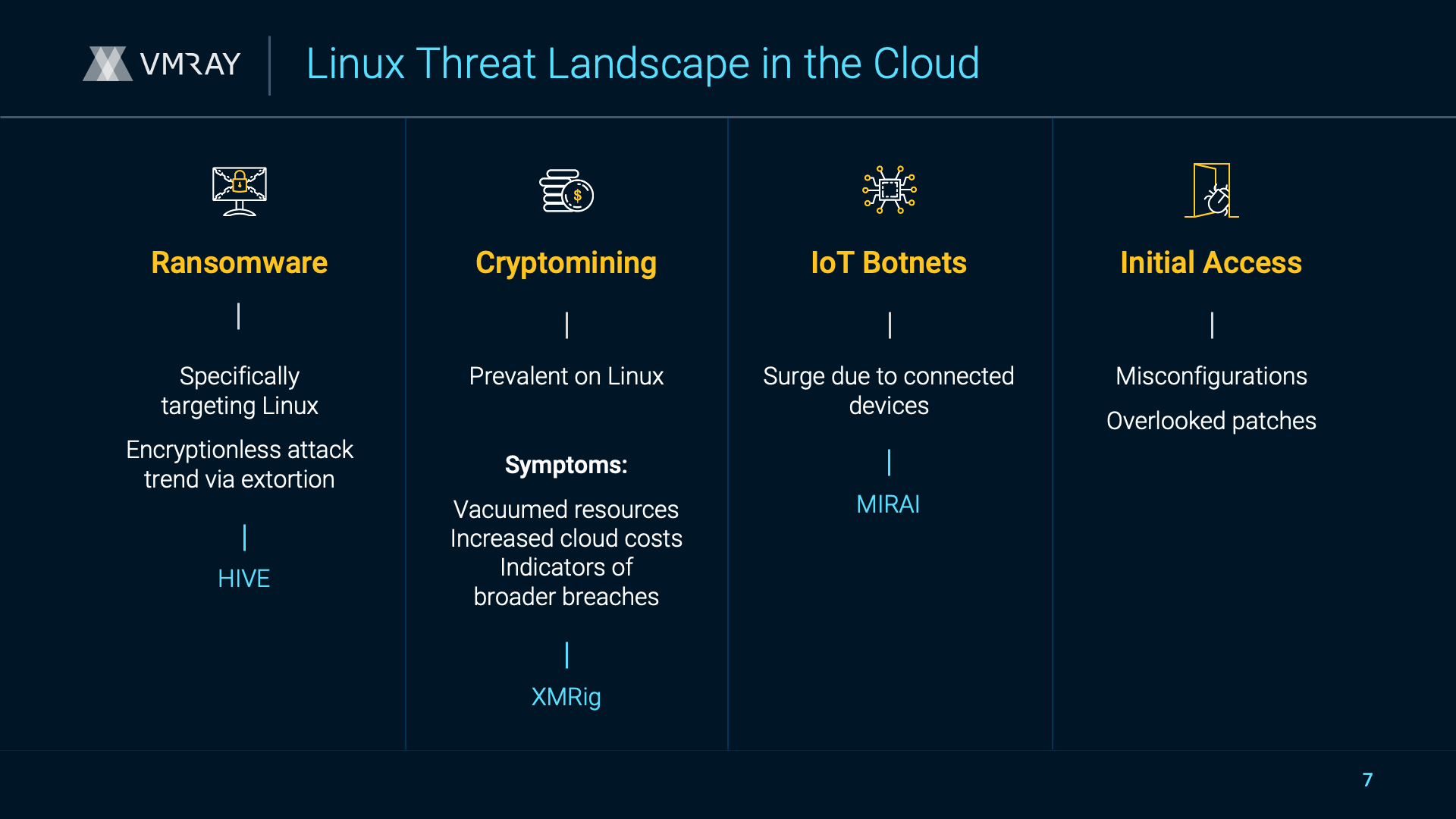
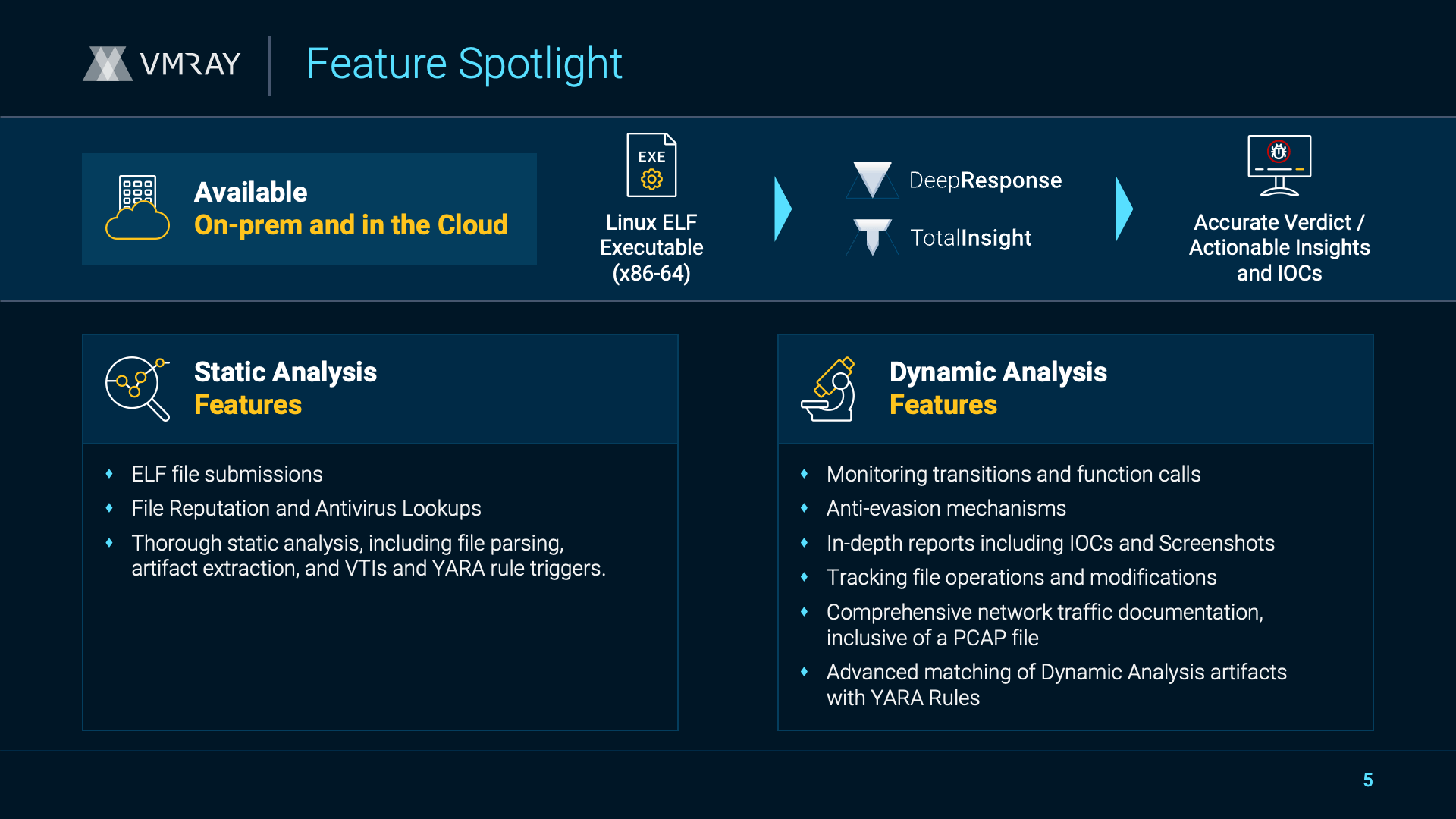
VMRay x VMWare Cloud EDR Connector
VMWare Carbon Black Cloud can upload all new binaries it detects to the cloud Universal Binary Store (UBS) so that nothing is missed during the investigation even if original malware or hacking tools were later deleted by intruders. All these new files may be automatically submitted to VMRay Analyzer for inspection. VMRay Analyzer performs analysis of the file and reports back to VMWare Carbon Black Cloud overall severity and IOCs. Link to a full analysis report from VMRay Analyzer is also available from the VMWare Carbon Black Cloud console.
Technical Description: Connector collects unique SHA256 hash values of processes and then downloads samples from CB Cloud UBS to submit them into VMRay Analyzer. After the analysis is finished, connector retrieves the results and in case the overall verdict is suspicious or malicious reports it back to VMware Carbon Black Cloud. A separate record is created in the VMRay Connector watchlist for every sample containing IOCs and VTIs associated with the sample. Full Analyzer report is also accessible from the VMware Carbon Black Cloud console.
Download the connector at: https://github.com/vmray/cb-cloud-edr-vmray-connector