Faster investigations, higher-confidence verdicts, and in-depth evidence that add clarity to your SOC, CERT and CTI workflows.
Use the most powerful threat analysis and detection platform against novel, targeted and evasive threats.
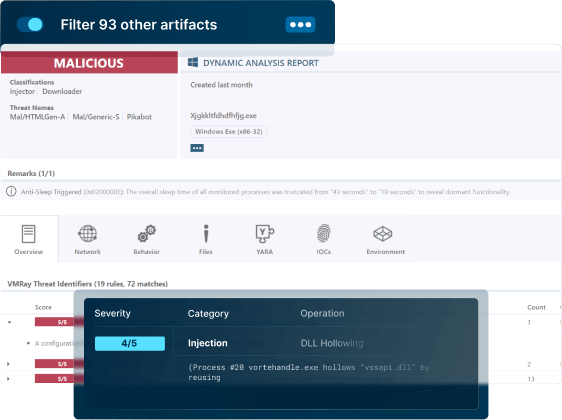



Because your SOC, CERT and CTI team are only as good as the data they get.



Detect and analyze novel, targeted, and evasive malware and phishing threats with sandbox-based and AI-assisted analysis solutions.

Actionable malware intelligence feed – without the noise.

VMRay gives you real choice — without compromising capability or privacy
Automate security tasks. Accelerate response. Enable threat intelligence.
A solution platform that grows with your needs.
Recent examples of novel, zero-day malware or phishing threats that we found earlier than most others.
Recent zero-day malware detections
Learn more about the threat landscape from our latest Threat Detection Highlights webinars
Boost the value of your existing security solutions by bringing the power of the most advanced threat detection and analysis platform into your EDR, XDR, SIEM, SOAR and TIP with connectors or rest API.
Helping the most demanding security teams across tech, finance, government, automotive, and beyond protect their organizations and achieve lasting results.
See how organizations worldwide have transformed their security operations with VMRay.
Hear directly from our customers how VMRay empowers their teams to detect, respond, and stay ahead of threats.
“Typically, in the past, we might have had to wait hours or even days for L2 or L3 teams to investigate such an attack but with VMRay I can have that done in less than 15 minutes.”

Principal Security Solutions Architect Expel
“ VMRay gave us confidence not just in data privacy but in investigative depth. It’s the most used tool in our security organization—every single day.”

Christopher King, Senior Director Northwestern Mutual
“As a reverse engineer, this product has enabled me to decrease manual analysis frequency and time, and increase positive identification of malware samples.”

Gartner Peer Insights 5* Global Retail Giant

Manager - Cyber Threat Intelligence Turkiye Is Bankasi
Uses advanced AI to stay ahead of emerging threats.