Uncover hidden malware threats effectively with laser-sharp IOCs and extensive behavioral analysis.

Global Top 10 Technology Company | Threat Intelligence Team




Accelerate Incident Response with VMRay
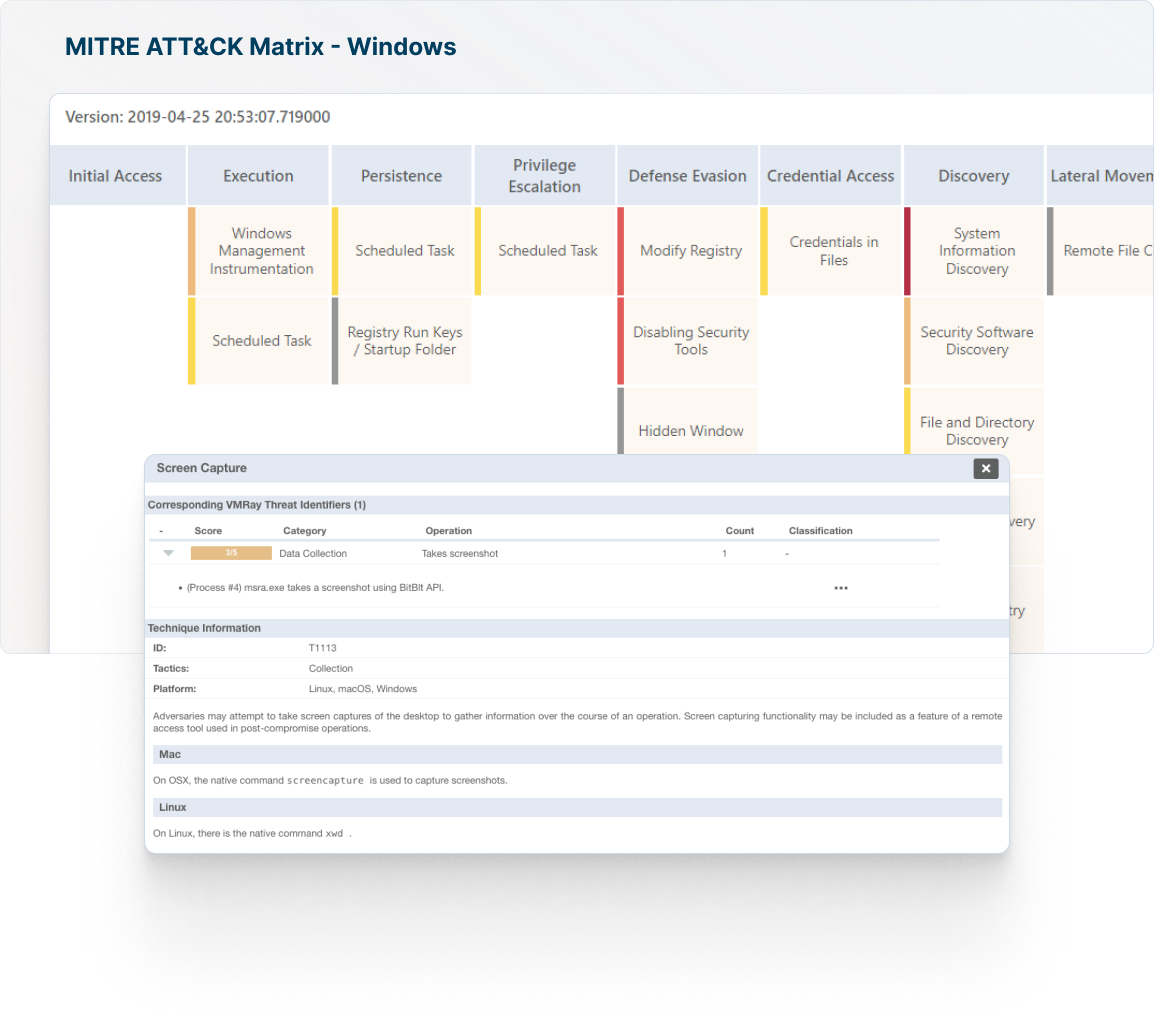
Enable proactive hunting with MITRE ATT&CK techniques automatically mapped to VMRay Threat Identifiers (VTIs) as part of the in-depth malware sandboxing process.
Run more effective queries on your detection tools as part of your hunting hypothesis.
Utilize behavioral maps and raw function logs from VMRay to query your logs in EDR, Sysmon, or Windows Security Events, and uncover previously unknown threats.
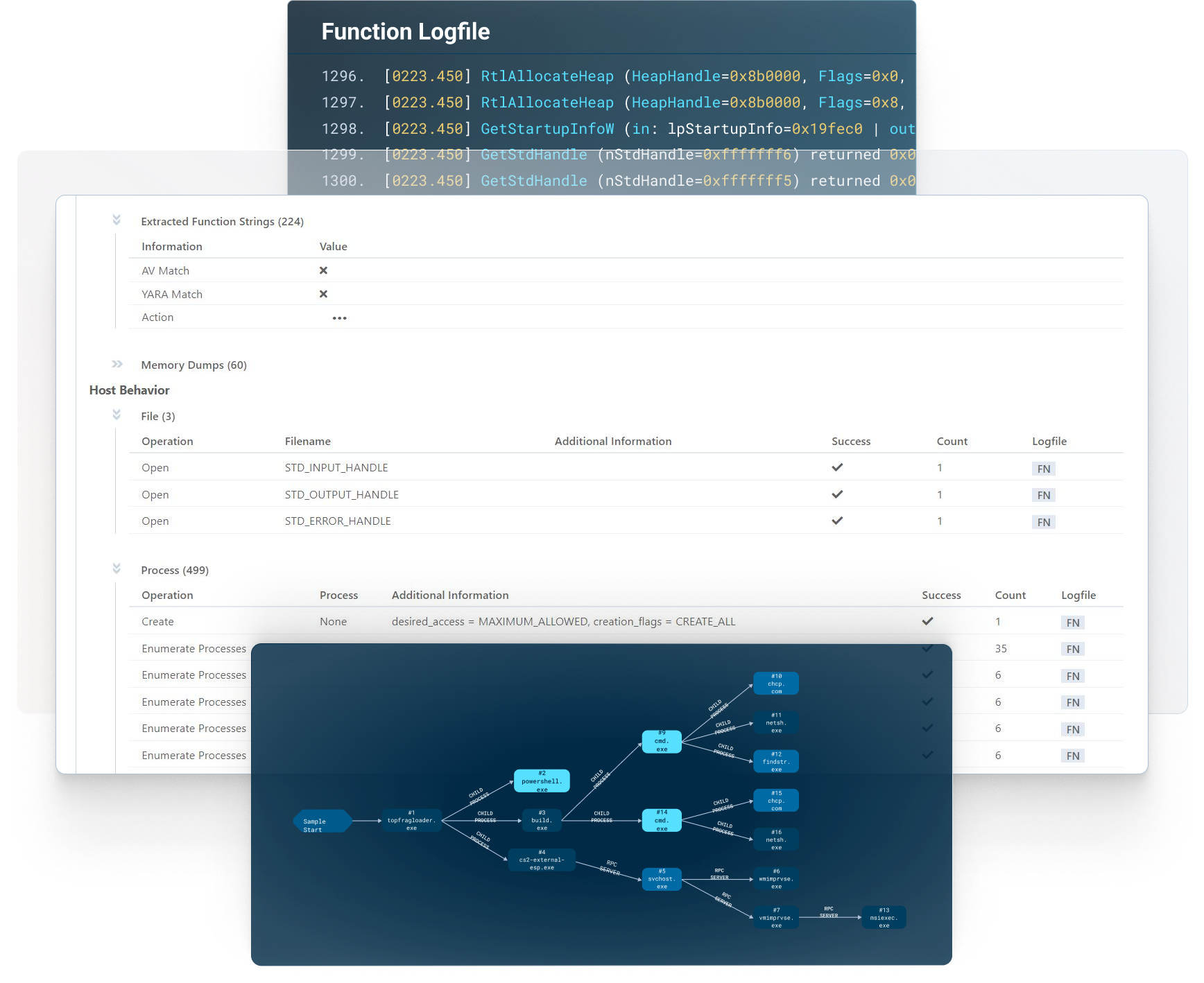



Threat hunting enables security teams to quickly ingest new threat intelligence, such as current indicators of compromise (IOCs) and articulate these indicators into queries across all applicable systems and networks. The results are then analyzed to identify suspicious activity that might require investigation or response.
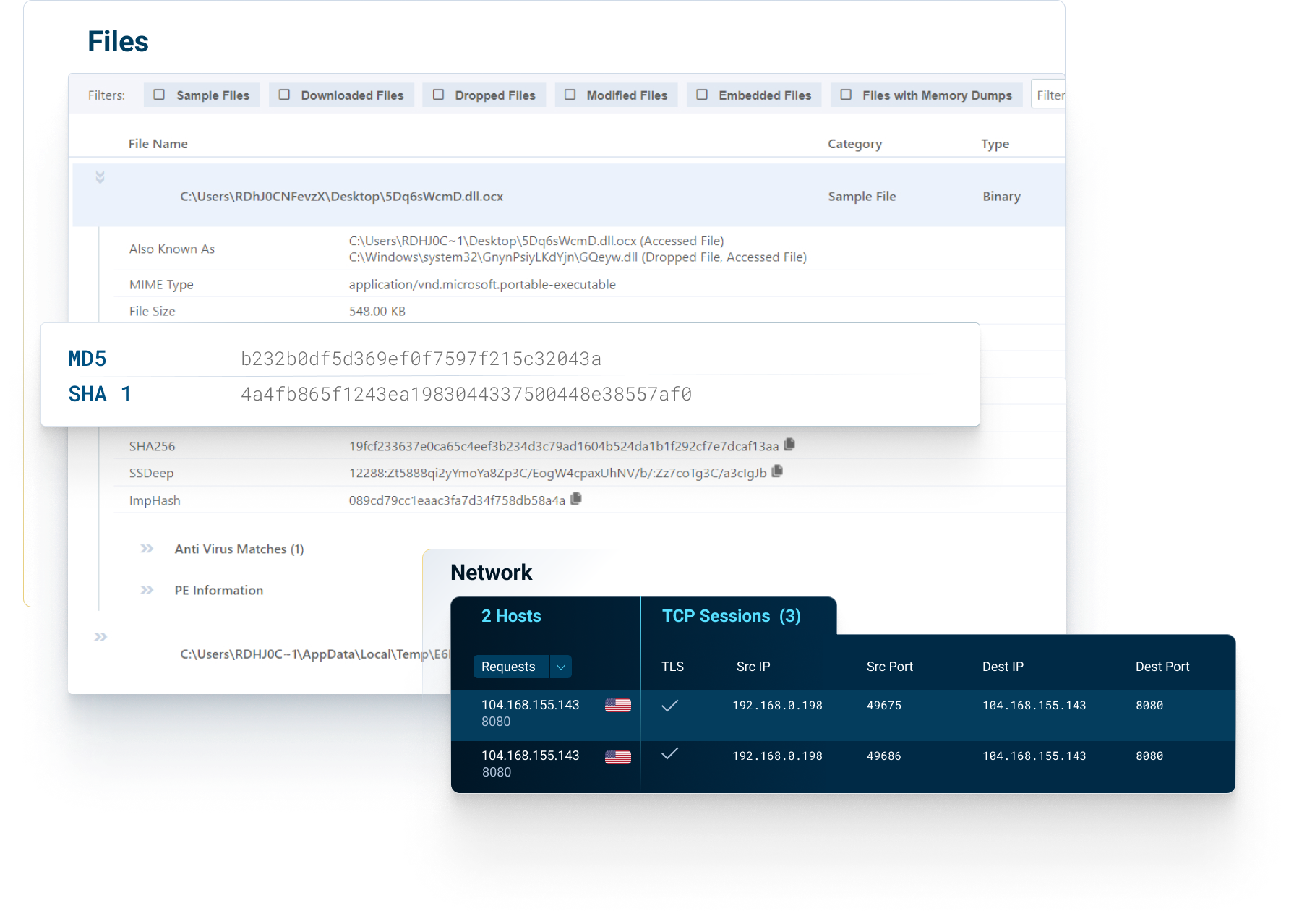
VMRay’s ability to identify both known and unknown Zero-Day threats using reputational, static, and dynamic analysis allows organizations to quickly extract the IOCs from binaries and URL’s that exhibit malicious behavior. These IOCs can then be used to hunt down compromised systems and identify encrypted Command and Control (C2) communications going to specific IP addresses. The IOCs can then be used by Detection Engineering Teams to create IDS signatures, Firewall rules, and email policy rules to mitigate future attacks.
VMRay integrates via API with the following EDR, XDR, SIEM, SOAR and TIP solutions.
EDR/XDR Integrations
SentinelOne, Microsoft Defender for Endpoint, and CrowdStrike
SIEM Integrations
Splunk SIEM, IBM QRadar
SOAR Integrations
Google Chronicle SOAR, Palo Alto Networks Cortex XSOAR, Splunk SOAR
TIP Integrations
Anomali, Cyware, MISP, ThreatConnect, ThreatQ
Yes. VMRay’s sandbox technology was built from the ground up with automation in mind due to the ever-increasing number of new attacks and threat vectors. VMRay’s automation includes automated malware triage and phishing, EDR/XDR malware alert enrichment and validation, integration into SOAR solutions to automate responses, and automated ingestion into TIP solutions for threat intelligence extraction.
VMRay’s value proposition goes beyond exceptional products, focusing on high-quality professional services and 24/7 customer support that eliminate skills gaps and drive success in dynamic cybersecurity environments to accelerate incident resolution.
Recognizing resource constraints faced by Security/IT teams, VMRay offers a comprehensive suite of services tailored for seamless onboarding, optimized configuration, and robust integrations – ensuring efficient deployment and maximizing solution efficacy.
VMRay addresses deployment concerns by offering a range of professional service offerings to get you up and running quickly. We leverage our expertise deploying hundreds of customers to ensure that you are up and running regardless of how complex your requirements may be.
X-press Onboarding
Our express onboarding service ensures a swift deployment while our expert team assists with configuration and provides guidance. Whether you’ve selected to utilize the VMRay Cloud or and on-premises solution, we will work with you to get the VMRay platform set up and configured to your requirements.
Automation Integration Deployment
Seamlessly integrate our solutions with your existing tools to enhance incident automation and strengthen your cybersecurity infrastructure. If your needs include taking advantage of the time and labor savings of integrating VMRay into your security ecosystem, we will work with you to configure our range of connectors to 3rd party platforms to other solutions within your environment.
Bespoke Training
Empower your team with tailored training options, including video recordings, accessible PDF materials, and in-person sessions. Basic training is provided during the on-boarding process and a variety of free training resources, both documentation and videos. Sometime customers want a more customized training solution to better align with their incident response plans. We will work with you to understand your specific requirements and deliver customized instructor based live training tailored to your specific needs.
The VMRay cloud-based platform receives reputational and static engine updates as they become available and are automatically uploaded to the cloud by VMRay.
The Dynamic Analysis uses thirty different types of technology including thousands of YARA Rules to identify malicious behavior. New YARA rules are created and added frequently between each major quarterly release to ensure the platform reflects the current and evolving threat landscape.




