Triage and enrich alerts from your email security stack.
Analyze user-reported emails—automatically, deeply, and reliably.
Finally, a sandbox built for phishing.
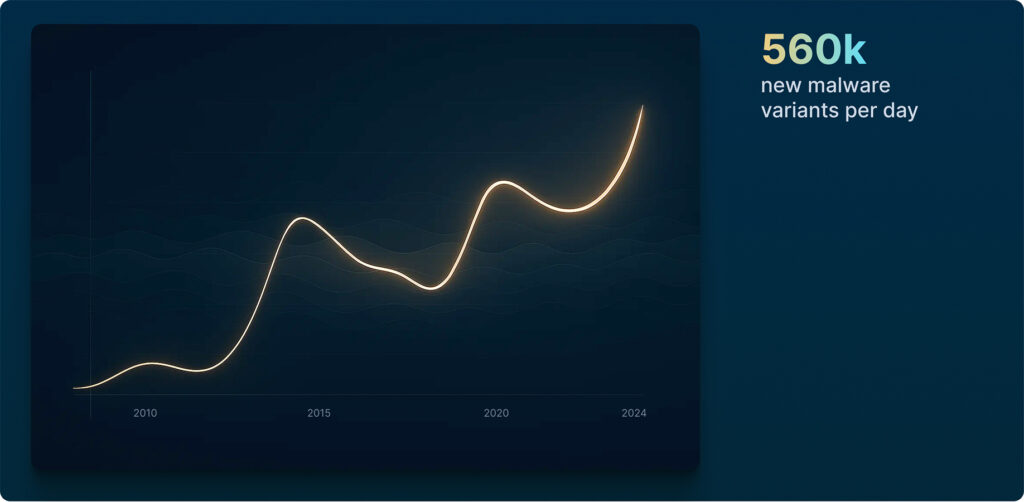
Millions are spent in prevention.
Yet still, 94% of breaches are due to phishing attacks.
Phishing threats get stronger. Faster.
AI-powered phishing is here:
faster campaigns, lower effort for attackers.
Phishing as a Service
makes new campaigns faster to build, harder to detect.
Unknown, zero-day
phishing threats emerge faster than legacy tools can keep up.
Phishing gets in.
Alerts pile up.
Speed over depth:
built-in sandboxes aren’t built to go all the way down the rabbit hole
Evasive techniques,
URL redirects behind documents or QR codes, and multi-step delivery chains fly under the radar
Thousands of alerts are blocked.
So are your business processes.
The user did their part.
Can you?
It already passed through the first layer of defense.
You need better for the 2nd line.
Signature, AV, reputation or “good enough” sandbox
won’t help anymore.
You have a backlog of reports, and
impatient users who can’t wait to “click”.


“The most important capability in our investigative toolkit is VMRay.
Whether it’s investigating a suspicious link that redirects to a credential harvester or a suspicious Microsoft Word document – VMRay allows us to detonate samples safely and generate a detailed report of the activity.”
Ray Pugh
Director, Security Operations
Expel
VMRay’s abuse mailbox for
user reported phishing
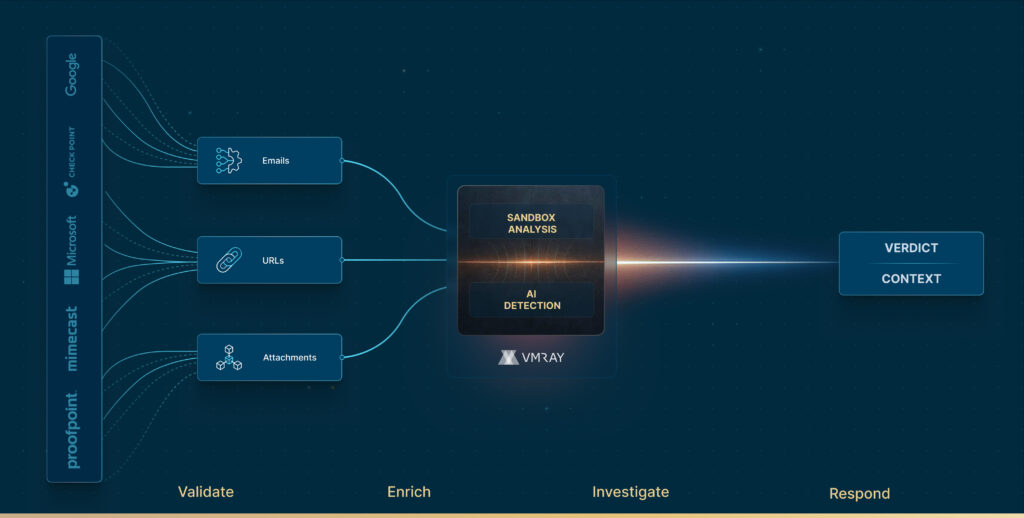
User-reported phishing emails create pressure on SOC teams.
VMRay automates their analysis, delivering fast and reliable verdicts—before users click or business gets disrupted.



even against unknown, zero-day phishing threats

Let your SOC breathe.
Let your business flow.
Turn phishing alerts to actionable intelligence.
Full control over your data.
No third-party sharing.
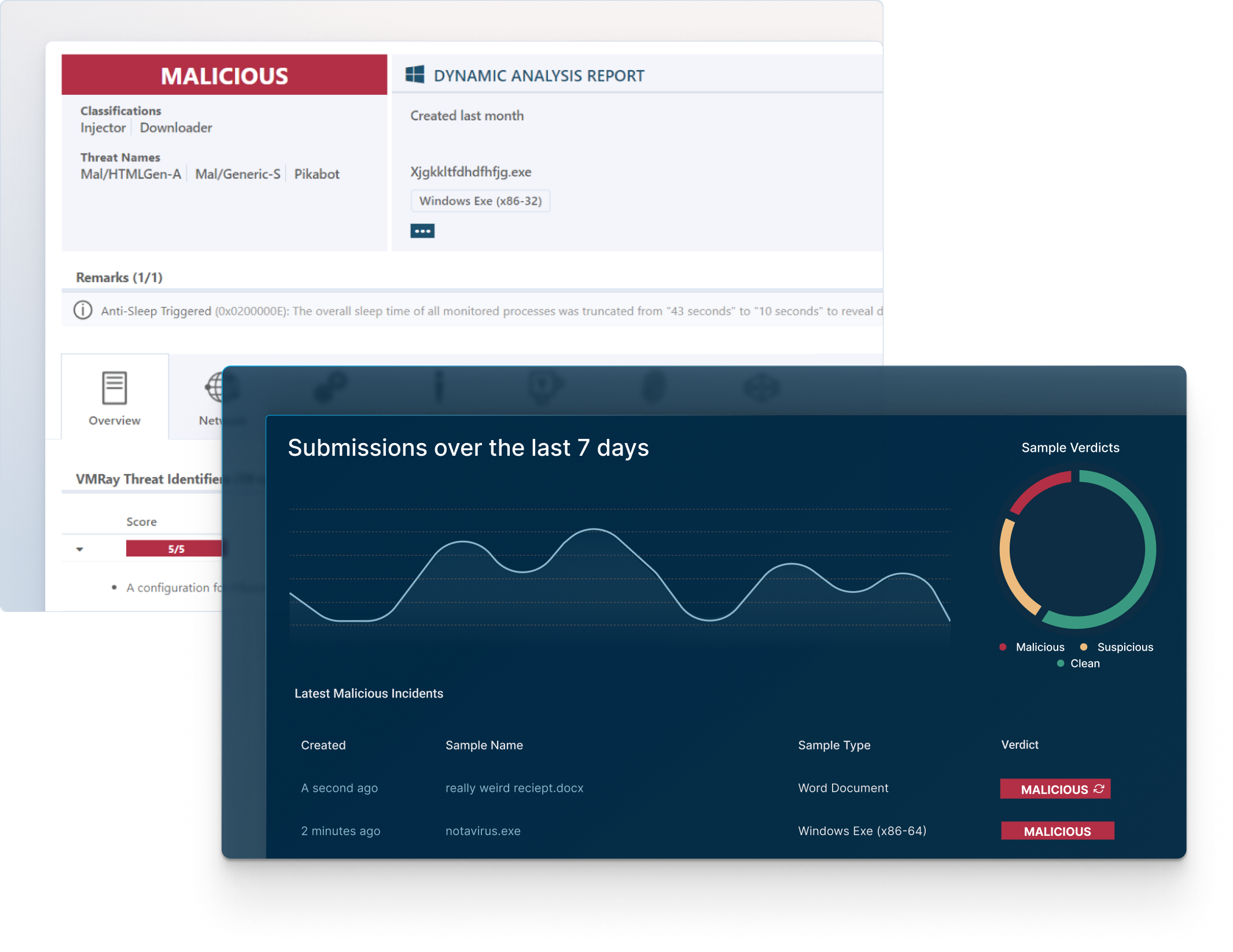
VMRay’s safe detonation and Machine Learning (ML) driven phishing analysis provides a definitive verdict with greater visibility into an email’s malicious actions.
Best-in-class reputational, static, and dynamic analysis of phishing and credential harvesting related email attacks.
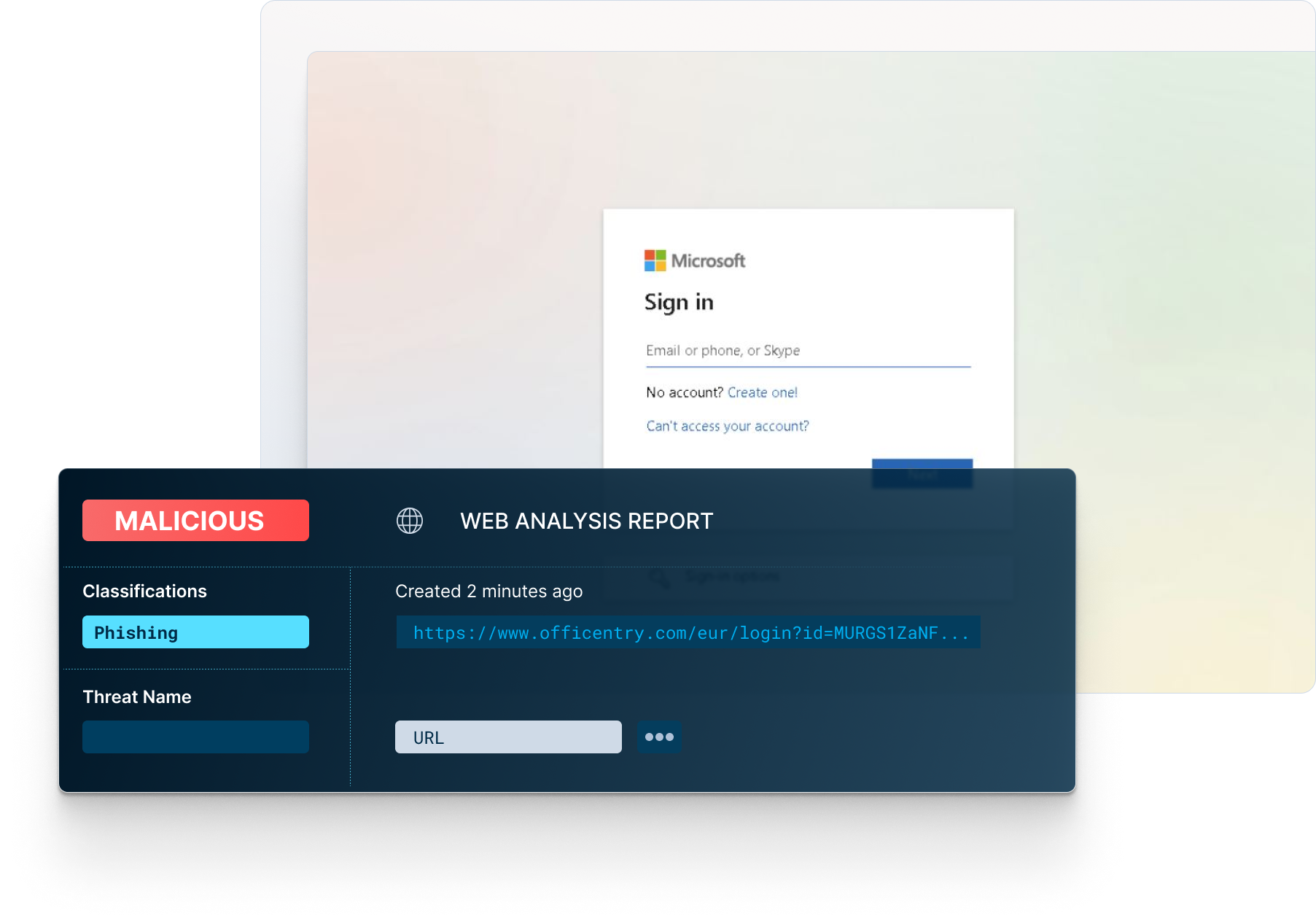
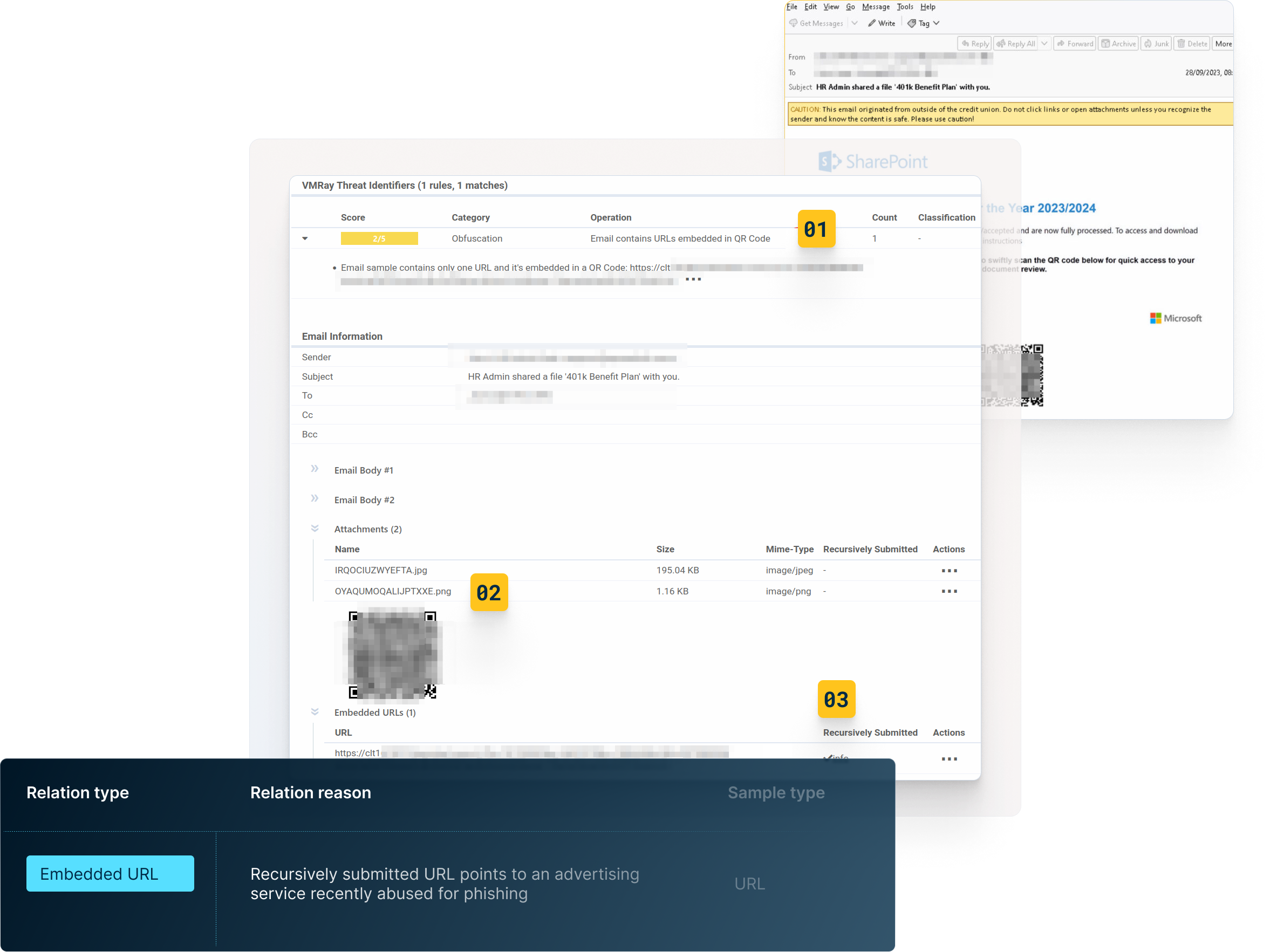
VMRay’s deep content inspection, recursive link analysis, file attachment verdicts, Smart Link, and other detected web objects can quickly identify emails with malicious intent.
Automated responses to end-user submissions reduces phishing related calls to the SOC and speeds the triage process without utilizing critical SOC team resources.
User Reported Phishing helps organizations identify malicious emails that have bypassed their perimeter email security or point phishing solution. Through a combination of end-user education and technology, malicious emails can be identified and forwarded by the end-user to an Abuse Mailbox.
The difference between VMRay’s User Reported Phishing and other vendor solutions stops there. Other vendor solutions require a SOC Analyst to then manually triage the email to identify if it is malicious or not. The results of the process may take hours or days depending on the volume of emails received by the Abuse Mailbox.
VMRay differentiates against other solutions by automatically triaging and analyzing the email threat to determine if it is malicious or benign. If malicious, the SOC team is notified along with the analysis and extracted IOCs to mitigate the threat within minutes and the end-user informed. All without using SOC Team resources.
Integrating with an EDR/XDR/SOAR solution is the easiest way to implement Abuse Mailbox automation. Email threats that have bypassed perimeter email security and phishing solutions can be identified by end users educated in spotting email threats.
Once forwarded to the Abuse Mailbox and analyzed by VMRay, the EDR/XDR/SOAR integrated with VMRay can take automated response actions based on predefined playbooks or workflows if the reported email is a legitimate threat.
The IOCs extracted from the analysis can be used to create email policies, firewall rules, and detection signatures to mitigate current and any subsequent attacks.
The VMRay platform is hardened against direct attacks and constantly assessed for vulnerabilities and exposures that would allow a bad threat actor to penetrate the system. The VMRay Platform allows customers to create a completely isolated environment for analyzing advanced phishing threats, without the risks posed by open-source tools and services. With On-Premises deployments, customers can ensure their data never leaves the network.
VMRay offers two data center locations, one in the EU and the other in the US, to our customers. While located in different regions, both are ISO27001 compliant, meet GDPR and California Data Privacy Act standards for data protection and privacy, and meet the Singapore Monetary Authority guidelines for cloud services for the financial sector. Our customer data is protected in accordance with some of the strictest data privacy laws in the world.
Abuse Mailbox is compatible with any email system. Reported emails are forwarded to an Abuse Mailbox on the VMRay platform and automatically analyzed upon receipt. The results of the email attack analysis are then sent to the SOC team in addition to a notification of malicious or benign sent to the end user, typically within minutes.
Phishing attacks are responsible for 91-94% of successful breaches according to many industry leaders. Malware authors have developed many different methods to bypass static detection controls or methods that exceed the capabilities of vendor phishing solutions. For example, recursive embedded links in documents that go many levels deeper than the default settings of the detection control is a common tactic. Using QR-Codes that when scanned, lead to malicious websites with malware booby-trapped webpages.
VMRay’s Labs team work hard to keep up with the constantly changing threat landscape and the attack chain methods used by bad threat actors. Once a new Advanced phishing attack method is identified, VMRay updates YARA rules and Machine Learning engines to accurately identify these threats.




