
DeepResponse – Accelerating Malware Analysis and Sandboxing
Discover more about DeepResponse’ malware sandboxing capabilities

FinalVerdict – Timely Insights into Malware and Phishing Threats
Explore FinalVerdict’s advanced malware & phishing analysis capabilities

TotalInsight – Tailored Threat Intelligence against evolving threats
Learn more aboutTotalInsight’s dynamic analysis capabilities
Flexible and Customer-Centric:
Filter out the noise and get fast and reliable verdicts with the single source of truth to activate effective security automation rules and playbooks. Mitigate the effects of alert fatigue and skills shortage on your SOC team.
As of the 2023.2.0 update, products can be licensed for both Cloud and On-Prem customers.
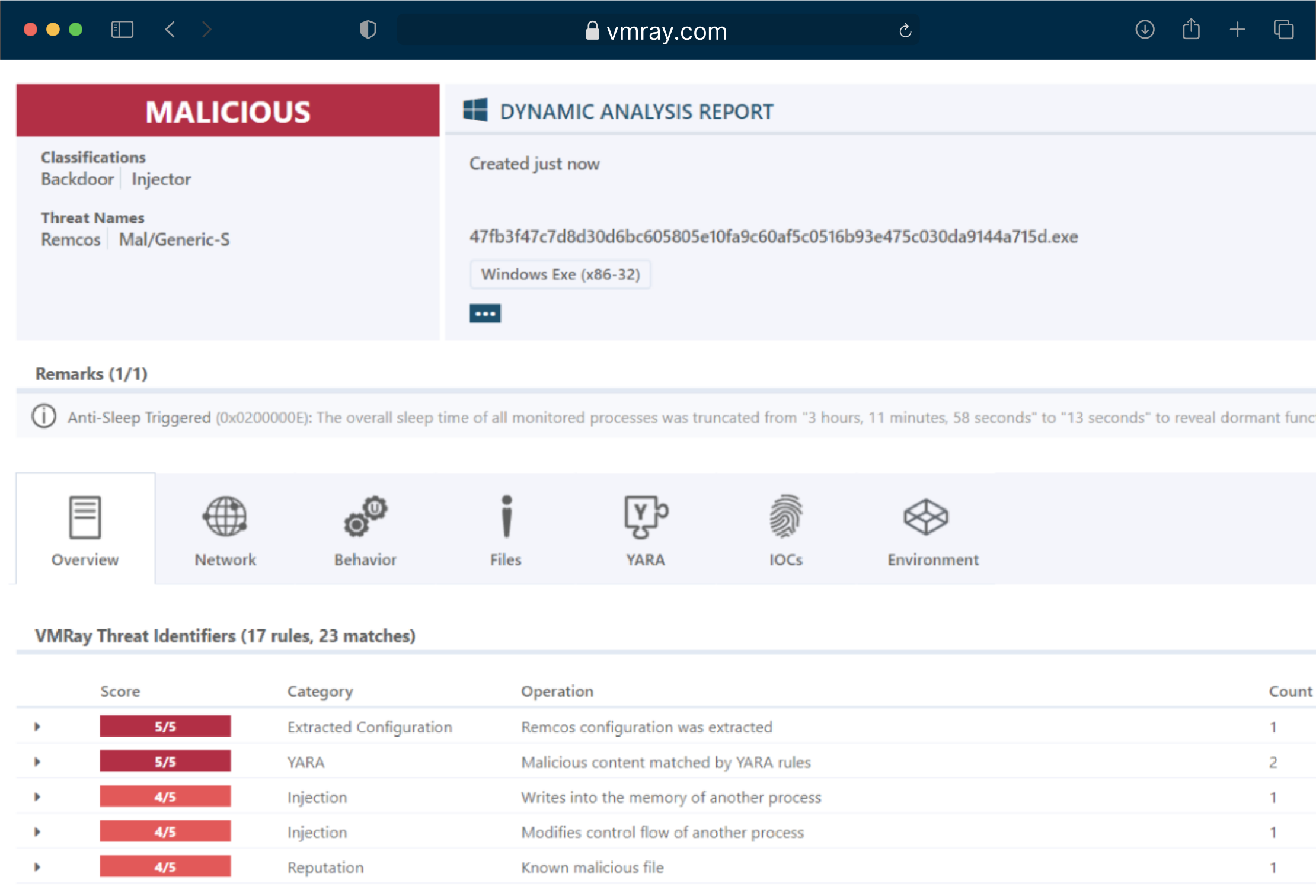
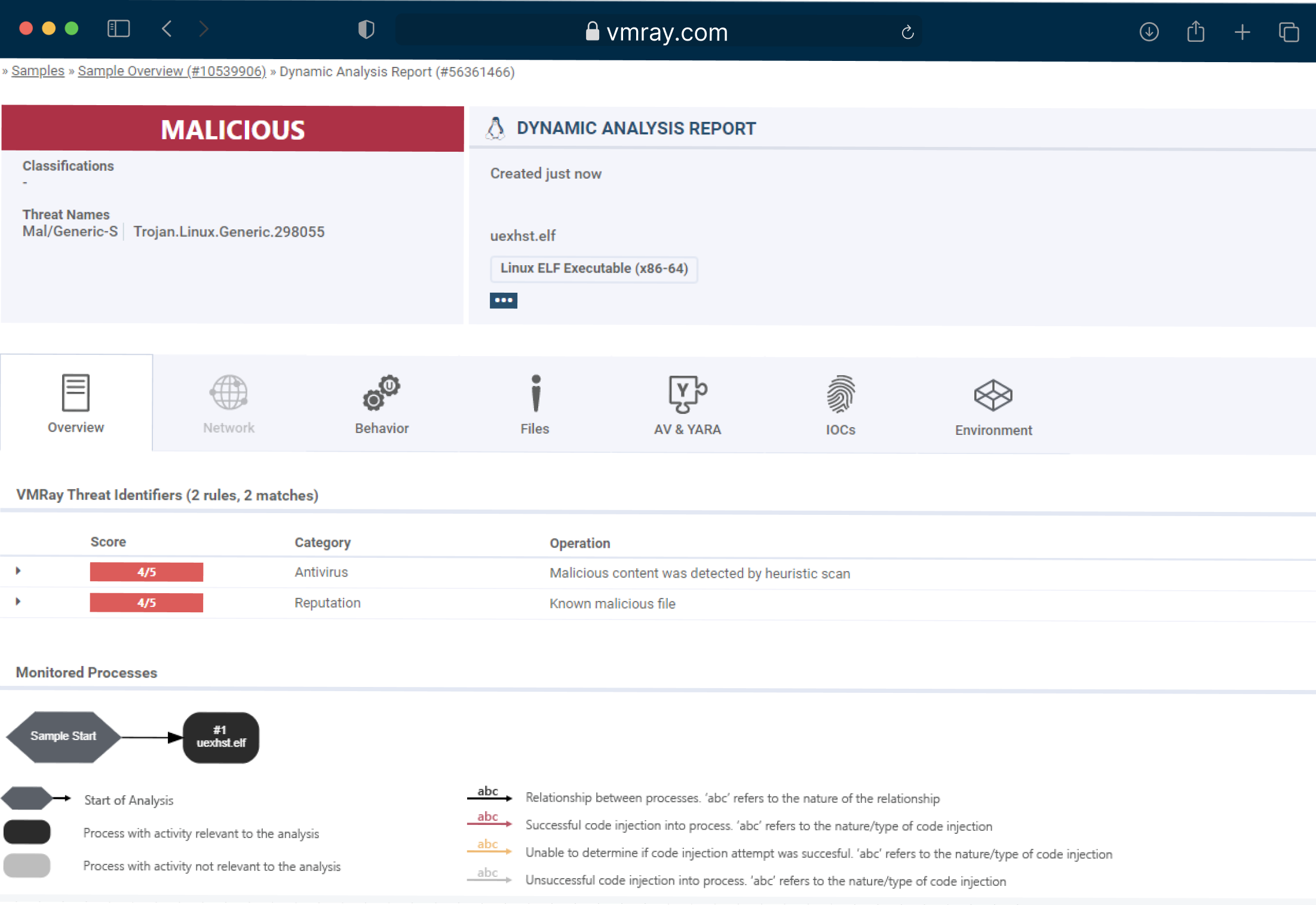
Transitioning Beyond the Capabilities of Analyzer
With the evolution from our legacy product VMRay Analyzer, we’ve expanded our offerings to address emerging challenges in cybersecurity, including Linux malware analysis.
Our new product portfolio includes advanced features to tackle Linux-based threats, which were previously not available with our Analyzer plans.
Check our latest insights on malware, phishing, sandboxing, AI in cybersecurity, and much more.
Browse the courses about alert handling, deep threat analysis and response, threat intelligence generation and more.
See real-world examples of VMRay’s best-in-class malware analysis and detection platform.




