

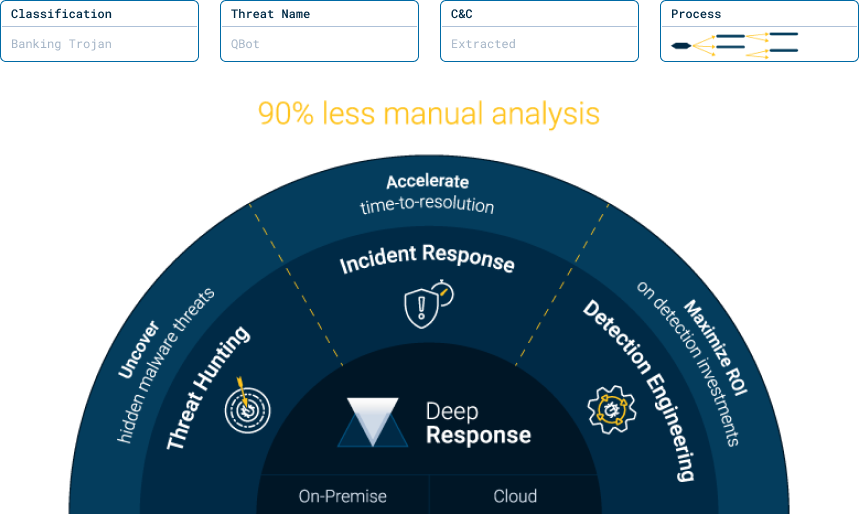
Up to 90% reduction in the time spent for manual analyses.
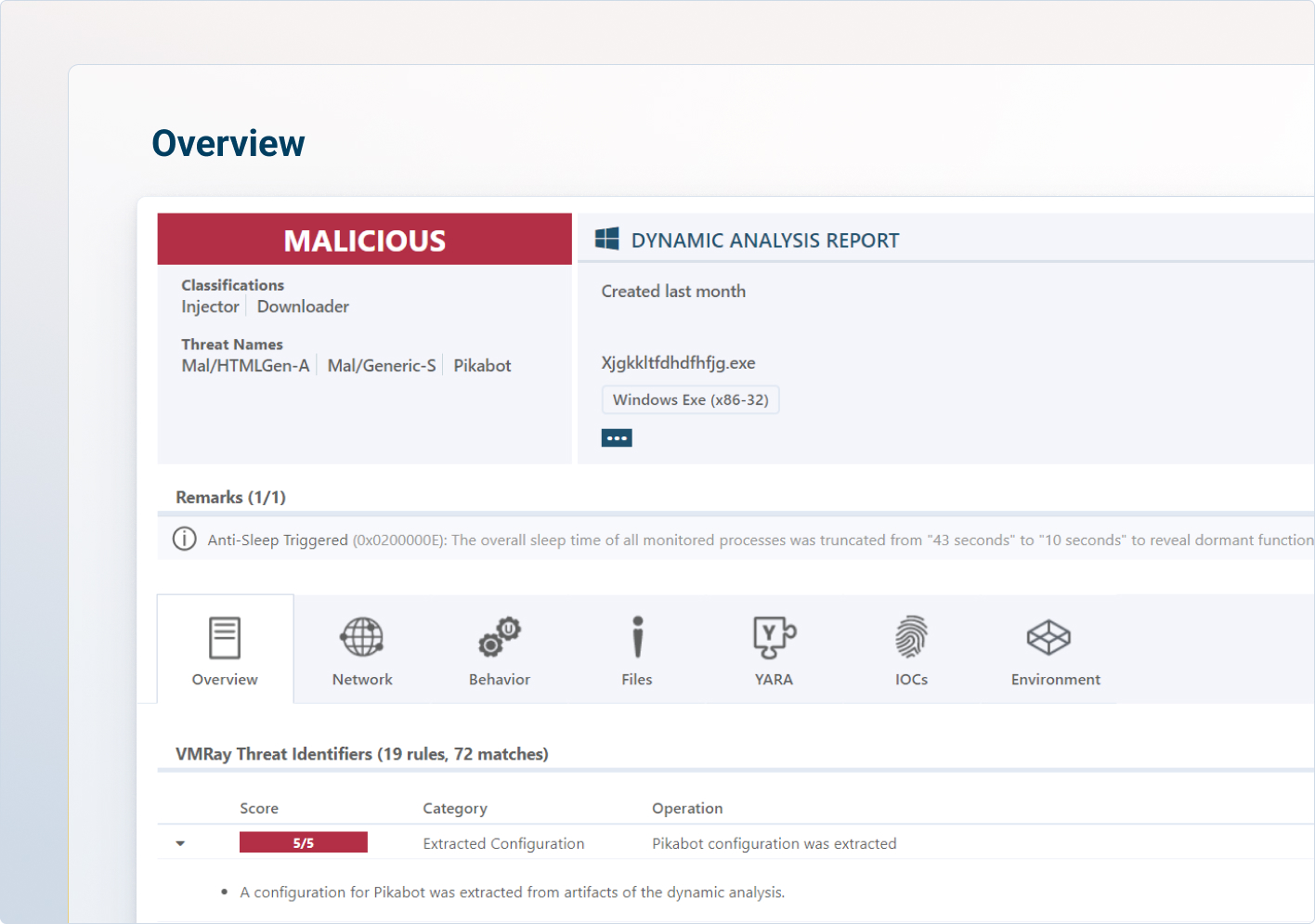
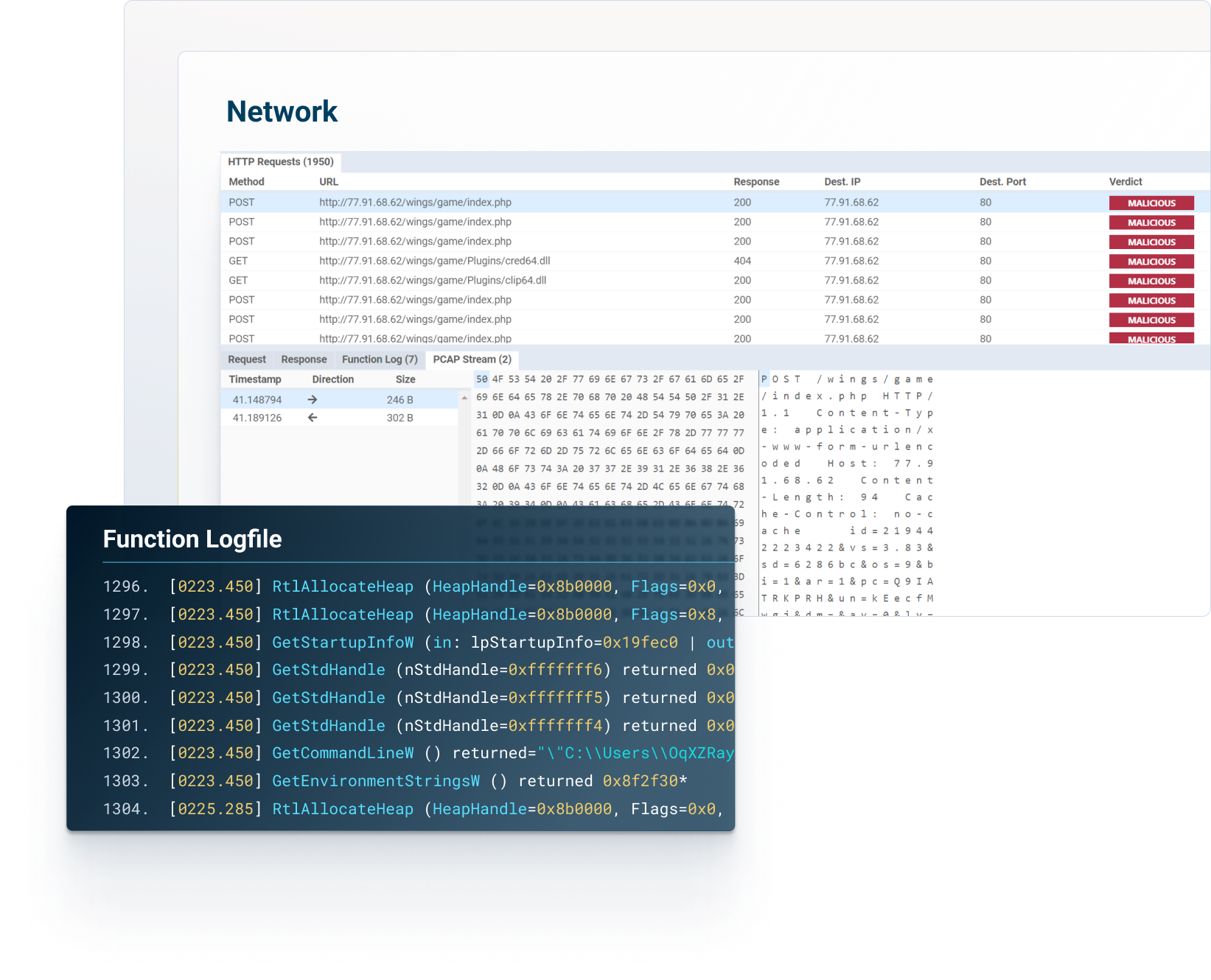
Complete invisibility to the threats and the full analysis until the last step of its execution.
Accurate & noise-free insights to help your analysts focus on what matters.
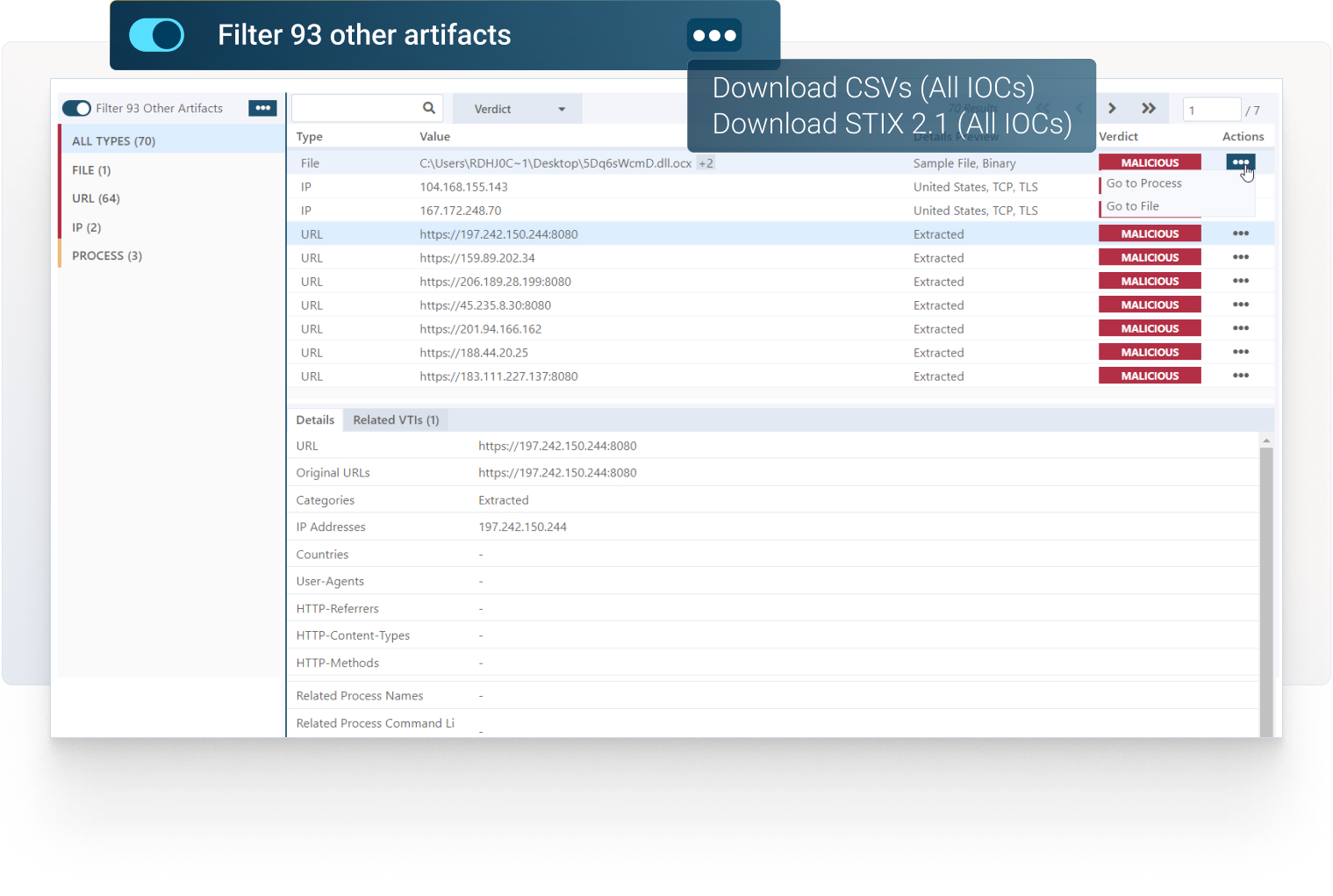
Proactive securtiy stance and lower barrier to classify malware families.
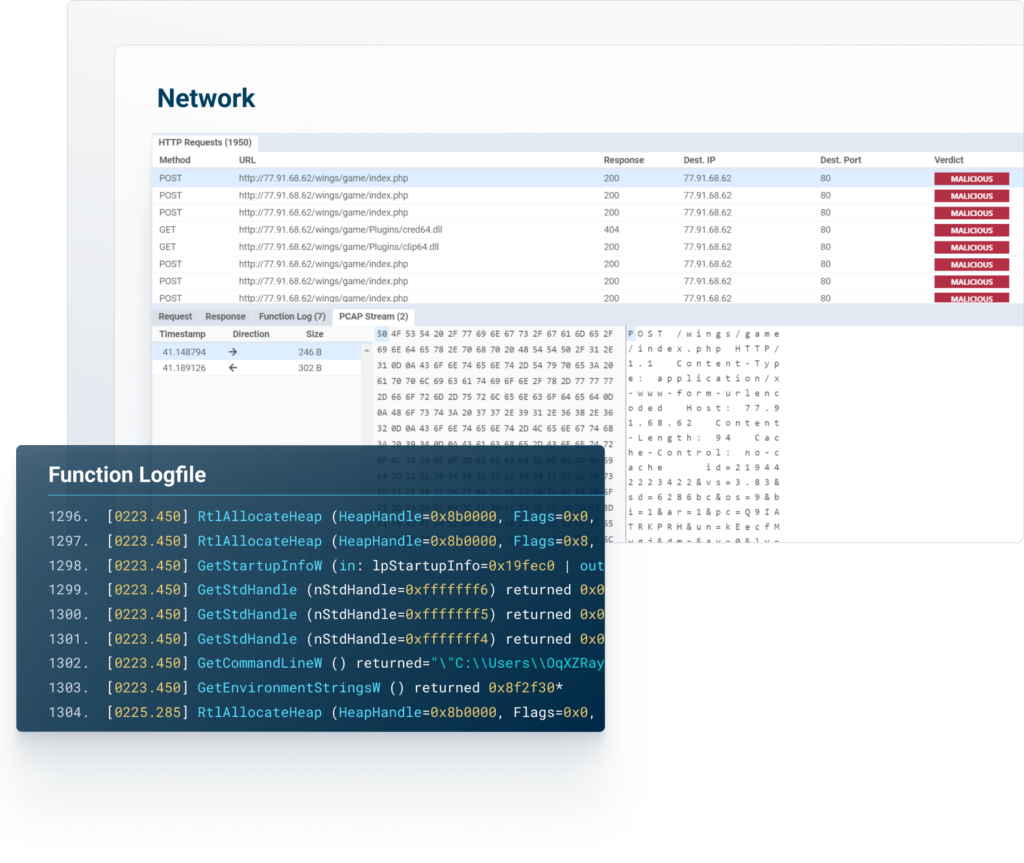
Check the full reports, explore the network connections, see the details on malicious behavior, map the threat on MITRE ATT&CK Framework, download IOCs and artifacts, and much more.
Your search for the better
sandbox ends here.
Explore the magic that sets VMRay apart and above.
With 30+ cutting edge technologies, VMRay is based on the most powerful sandbox that remains invisible to even the most evasive malware.
Precision & accuracy
made in Germany
Your data is yours.
Ultimate privacy.





Further resources
on advanced threat analysis




