



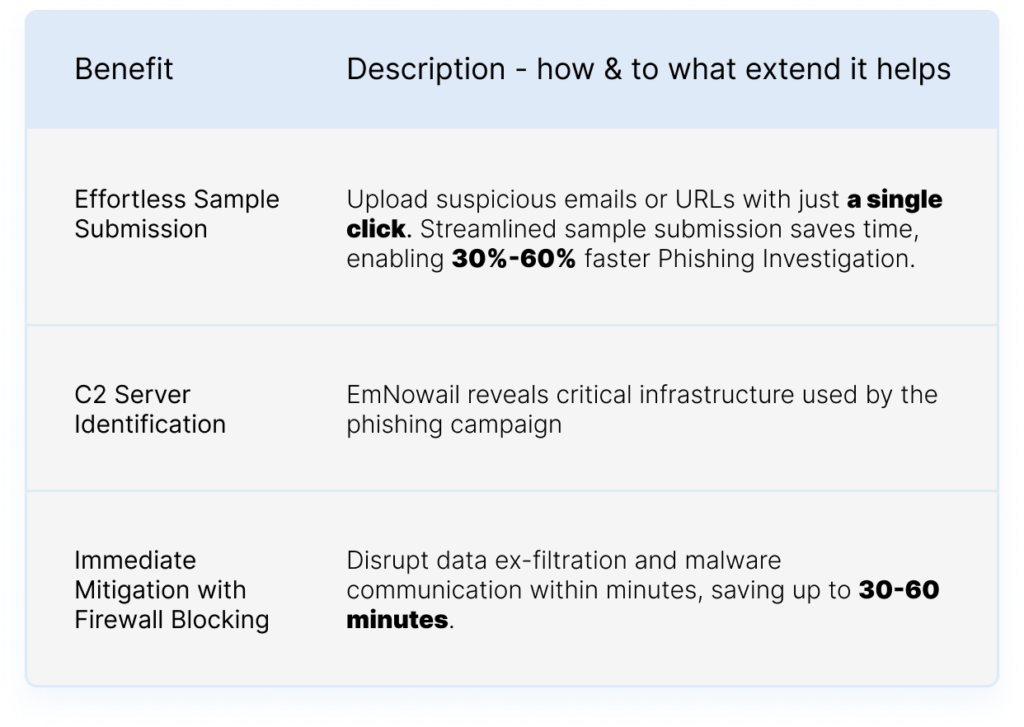
Rapid Verdicts
Interactive Analysis
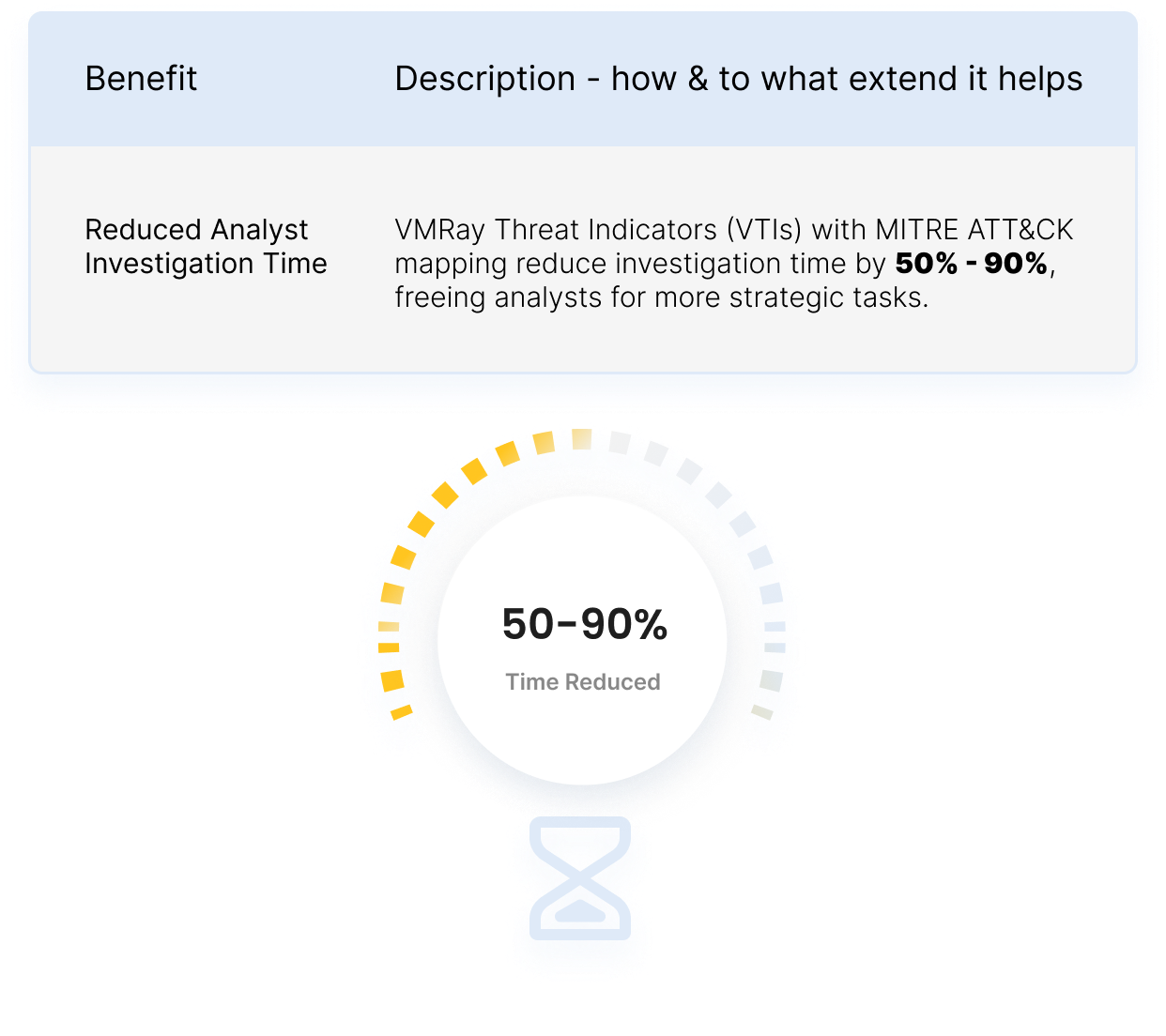
Isolate Faster
Complete Privacy
We Don't Share your Samples
Windows/Linux/MacOS Analysis Environments
EDR/SOAR/TIP Integrations
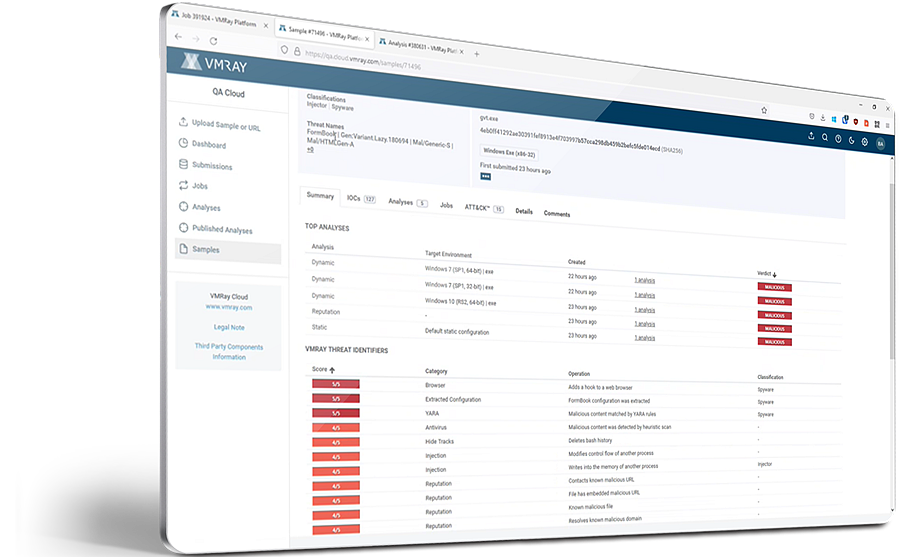
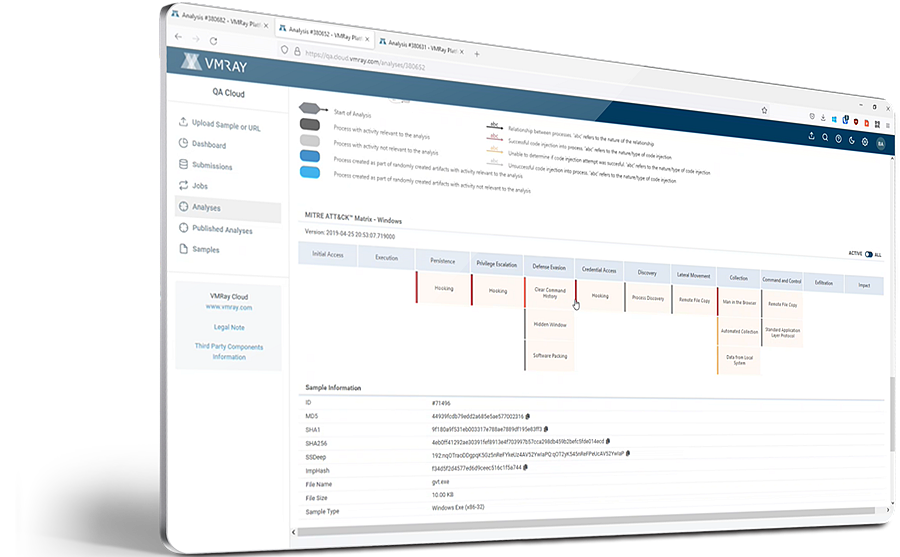
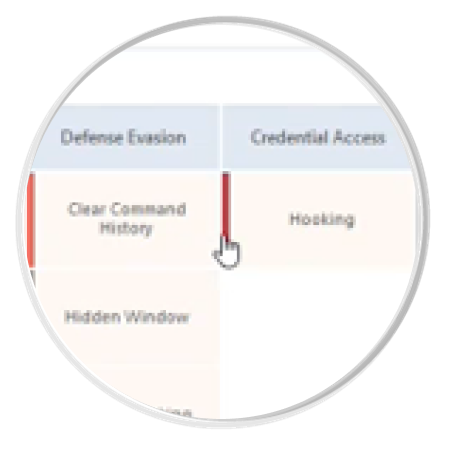
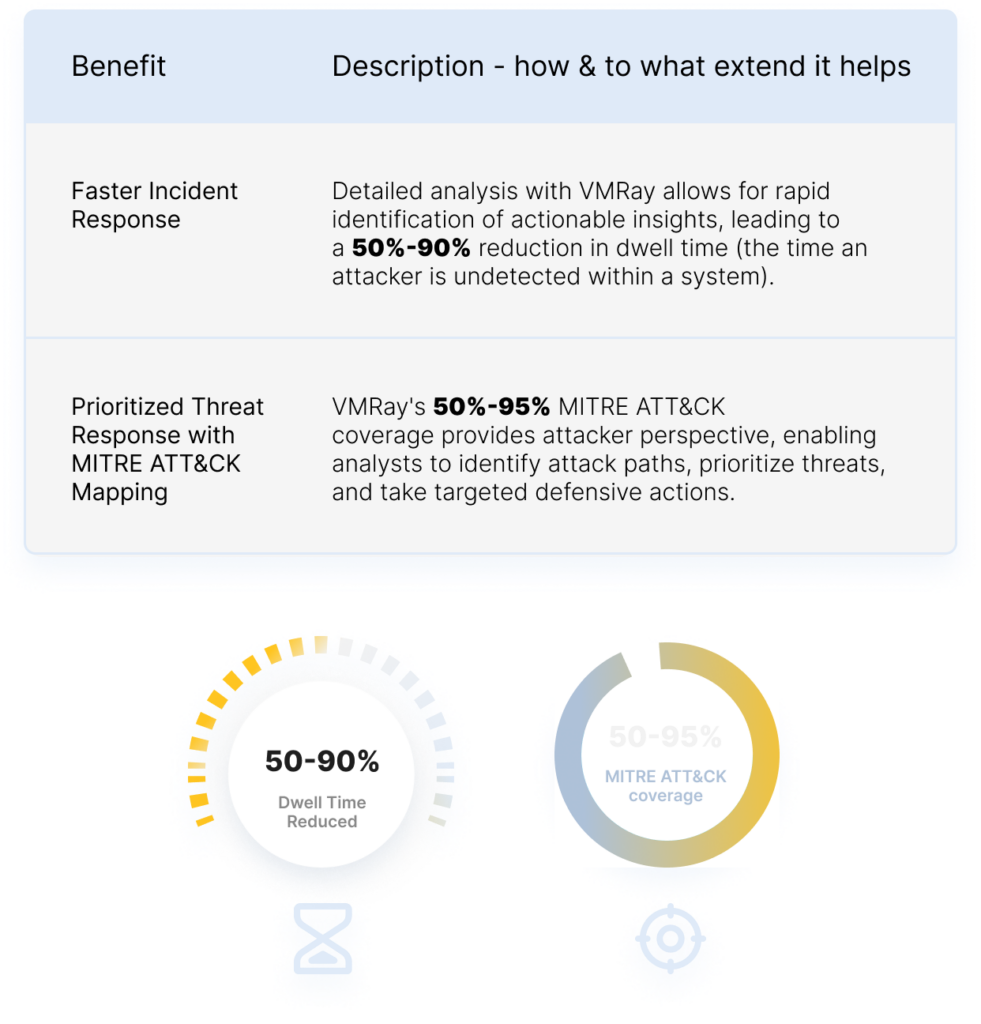
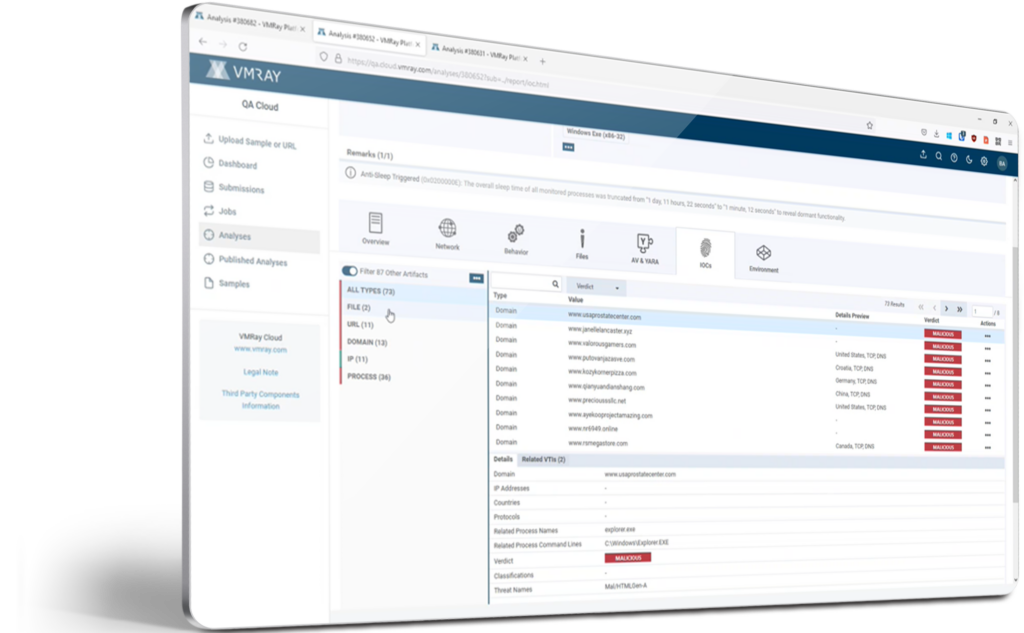
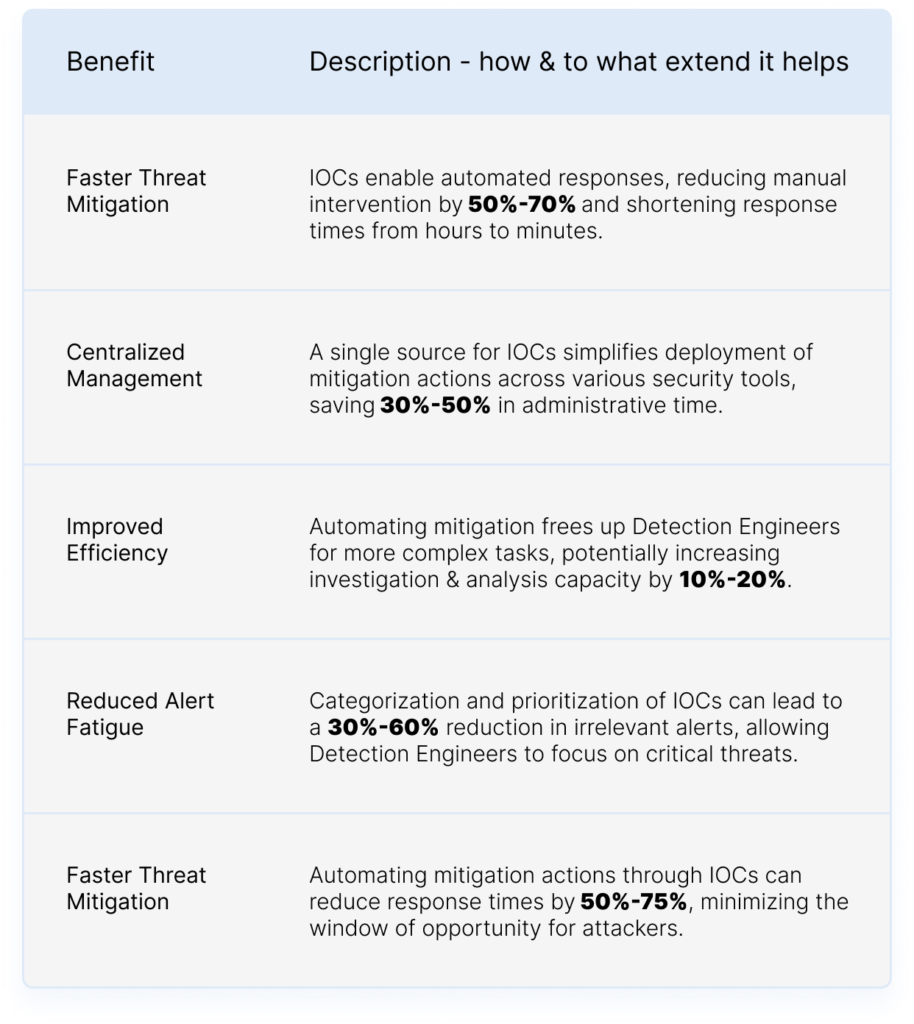
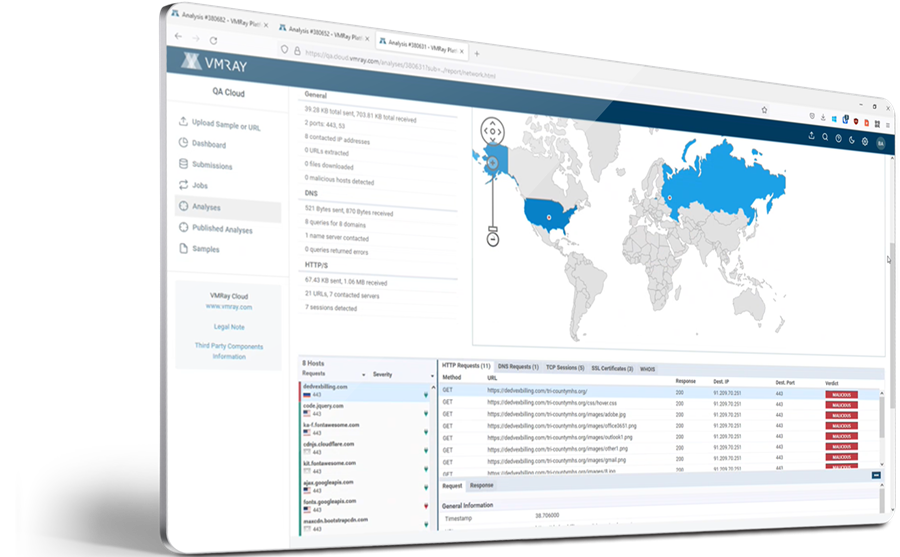
A VMRay malware analysis report provides:
VMRay can be deployed either cloud or on-premises.
VMRay Cloud and On-Premises both have the same core functionality and ability to analyze and detect malware. The main difference between Cloud and On-Premises is the level of customization offered.
VMRay On-Premises supports extensive customization of:
Check the report formats, see the overview, explore the network connections, details on the malicious behavior, map the threat on MITRE ATT&CK Framework, download IOCs and artifacts & more:




