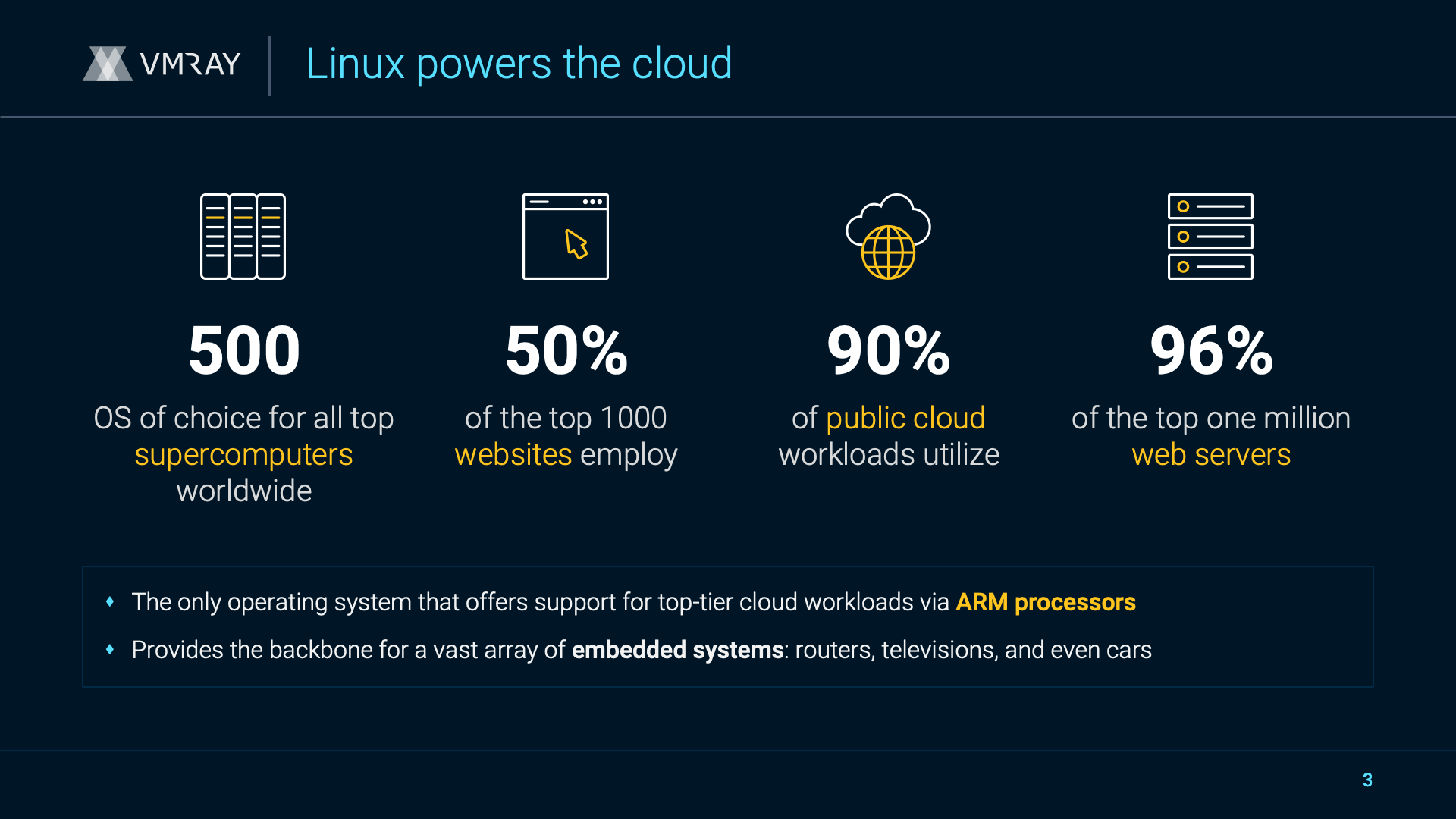
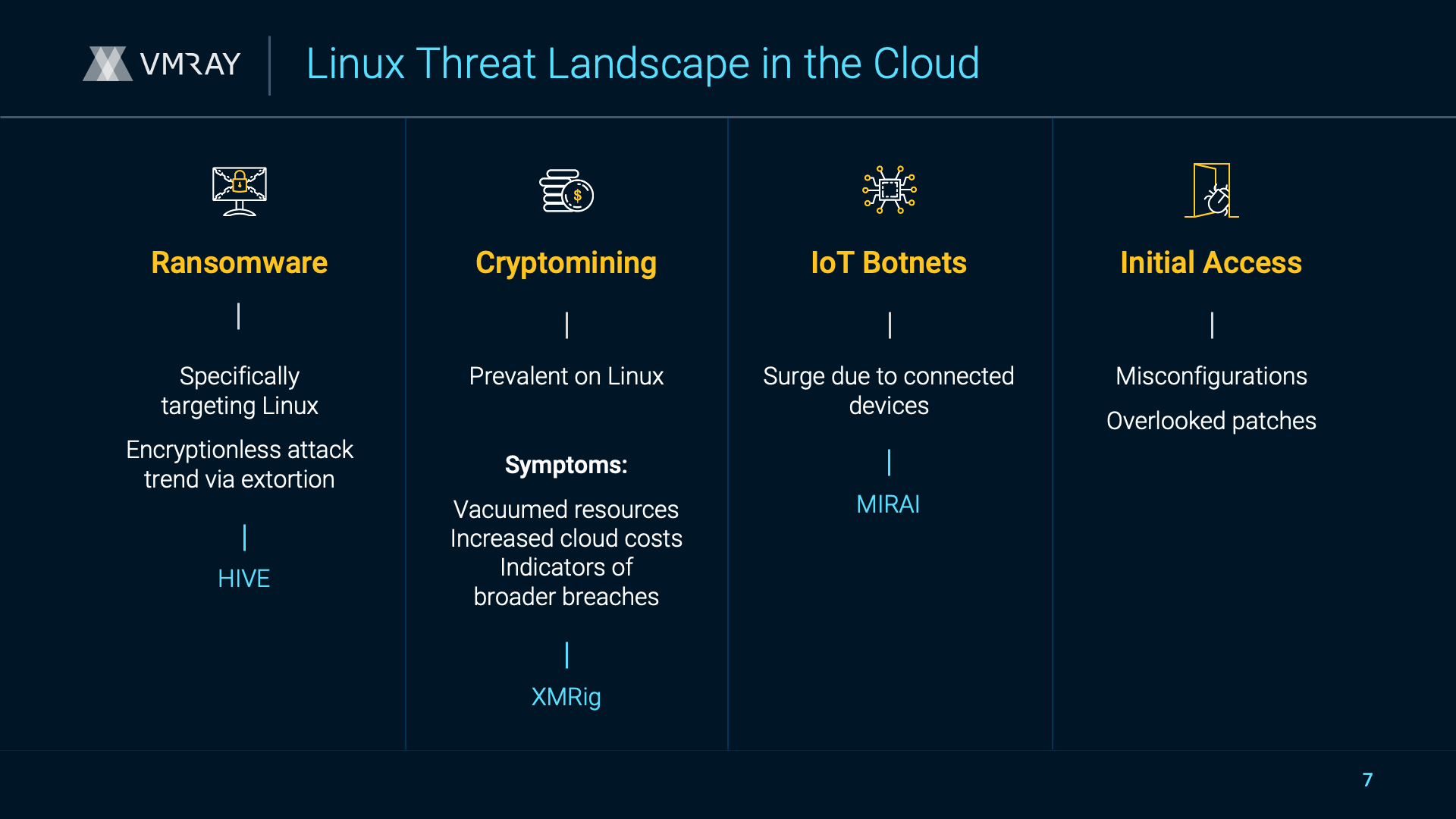
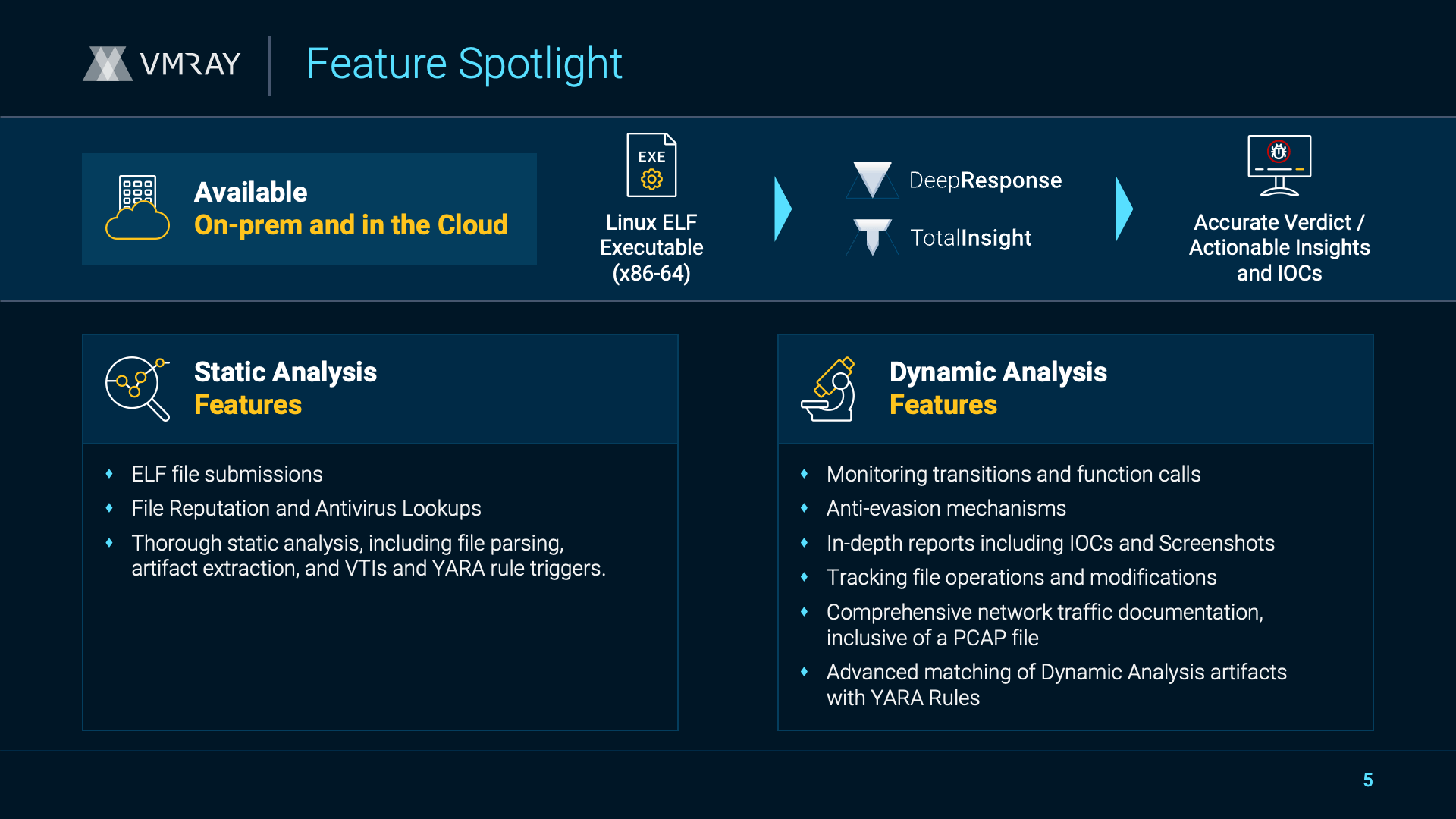
Incident response cases move fast. Analysts typically collect data from all corners of the enterprise, from registry hives to logs to malware samples. And while teams are good at collecting malware samples, many don’t have dedicated reverse engineers to turn those samples into actionable intelligence. It’s time to change course.
VMRay wants to transform automated malware analysis with its agentless hypervisor-based approach. SANS analyst, instructor, and incident responder Matt Bromiley has tested VMRay Analyzer and put it through its paces. In this webcast and paper, he shares his experience with the product, including:
Ease of use, including product layout and barriers to success
Efficiency of the rapid reputation engine to determine file maliciousness
Integration with IR team workflows and third-party products
How VMRay Analyzer handles multiple malware samples to provide quick and actionable answers to incident responders.
Watch this webcast to see how VMRay Analyzer can become an integral part of your incident response team.