rdfg546fgh.exe
Created at 2019-06-10T12:14:00
Remarks (2/2)
(0x200000e): The overall sleep time of all monitored processes was truncated from "1 minute, 10 seconds" to "10 seconds" to reveal dormant functionality.
VMRay Threat Indicators (16 rules, 49 matches)
| Severity | Category | Operation | Count | Classification | |
|---|---|---|---|---|---|
|
5/5
|
Local AV | Malicious content was detected by heuristic scan | 2 | - | |
|
|||||
|
|||||
|
5/5
|
Reputation | Known malicious file | 1 | Trojan | |
|
|||||
|
4/5
|
File System | Renames user files | 1 | Ransomware | |
|
|||||
|
4/5
|
File System | Modifies content of user files | 1 | Ransomware | |
|
|||||
|
4/5
|
YARA | YARA match | 6 | - | |
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
2/5
|
Information Stealing | Reads sensitive browser data | 1 | - | |
|
|||||
|
2/5
|
Injection | Writes into the memory of a process running from a created or modified executable | 1 | - | |
|
|||||
|
2/5
|
Injection | Modifies control flow of a process running from a created or modified executable | 1 | - | |
|
|||||
|
1/5
|
Process | Creates process with hidden window | 2 | - | |
|
|||||
|
|||||
|
1/5
|
Process | Reads from memory of another process | 1 | - | |
|
|||||
|
1/5
|
Process | Creates a page with write and execute permissions | 1 | - | |
|
|||||
|
1/5
|
Persistence | Installs system startup script or application | 1 | - | |
|
|||||
|
1/5
|
Masquerade | Changes folder appearance | 26 | - | |
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
1/5
|
Information Stealing | Possibly does reconnaissance | 2 | - | |
|
|||||
|
|||||
|
1/5
|
File System | Creates an unusually large number of files | 1 | - | |
|
|||||
|
1/5
|
Static | Unparsable sections in file | 1 | - | |
|
|||||
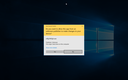
Screenshots
Monitored Processes
Sample Information
Analysis Information
| Creation Time | 2019-06-10 14:14 (UTC+2) |
| Analysis Duration | 00:04:31 |
| Number of Monitored Processes | 4 |
| Execution Successful |

|
| Reputation Enabled |

|
| WHOIS Enabled |

|
| Local AV Enabled |

|
| YARA Enabled |

|
| Number of AV Matches | 2 |
| Number of YARA Matches | 6 |
| Termination Reason | Timeout |
| Tags |