|
|
5/5
|
Local AV
|
Malicious content was detected by heuristic scan
|
1
|
-
|
|
|
-
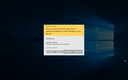
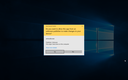
Local AV detected the sample itself as "Trojan.Ransom.Crysis.E".
|
|
|
5/5
|
YARA
|
YARA match
|
320
|
Ransomware
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\$GetCurrent\SafeOS\GetCurrentOOBE.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\$GetCurrent\SafeOS\SetupComplete.cmd.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1028\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1030\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1029\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1031\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1032\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1035\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1025\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1025\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1037\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1038\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1033\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1041\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1042\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1044\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1043\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1046\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1045\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1053\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1028\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1028\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1055\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1029\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1025\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1030\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1030\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1031\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1032\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1032\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1036\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\2070\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\3076\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\3082\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1040\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\DisplayIcon.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\Print.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1033\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1035\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1035\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1049\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\Rotate2.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\Rotate3.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\Rotate4.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\2052\SetupResources.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\Rotate6.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\Rotate7.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\Rotate8.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\Save.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1029\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1036\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1037\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1037\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1031\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1038\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1038\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1040\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1033\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1041\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1041\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1042\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\Setup.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\stop.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\SysReqMet.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\Rotate1.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\warn.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1036\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1043\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1043\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1044\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\Rotate5.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1045\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1045\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1046\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1040\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1049\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1049\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1042\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1053\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1055\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Graphics\SysReqNotMet.ico.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1044\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1055\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\2052\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\netfx_Core_x86.msi.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1046\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\2070\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\2070\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\1053\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\3076\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\3082\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Client\Parameterinfo.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Client\UiInfo.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\2052\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Extended\Parameterinfo.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Extended\UiInfo.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\3076\eula.rtf.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\ParameterInfo.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\header.bmp.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\SplashScreen.bmp.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\3082\LocalizedData.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\UiInfo.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\watermark.bmp.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\DHtmlHeader.html.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\BOOTSECT.BAK.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Boot\BOOTSTAT.DAT.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\RGB9RAST_x64.msi.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\RGB9Rast_x86.msi.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\SetupUi.xsd.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Strings.xml.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\Setup.exe.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\SetupUi.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\SetupEngine.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\SetupUtility.exe.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\588bce7c90097ed212\sqmapi.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Common Files\microsoft shared\Stationery\Desktop.ini.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\desktop.ini.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Java\jre1.8.0_144\bin\server\Xusage.txt.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Java\jre1.8.0_144\lib\deploy\ffjcext.zip.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Java\jre1.8.0_144\lib\deploy\splash.gif.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Java\jre1.8.0_144\lib\deploy\splash_11-lic.gif.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Java\jre1.8.0_144\lib\deploy\splash_11@2x-lic.gif.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Java\jre1.8.0_144\lib\jvm.hprof.txt.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Java\jre1.8.0_144\lib\tzdb.dat.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Java\jre1.8.0_144\lib\deploy\splash@2x.gif.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\Office16\OSPP.HTM.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\Office16\SLERROR.XML.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Java\jre1.8.0_144\Welcome.html.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\Office16\OSPP.VBS.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Logs\Application.evtx.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Logs\HardwareEvents.evtx.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00011_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00021_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00037_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00004_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00040_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00052_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00057_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00038_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00090_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00103_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00120_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00126_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00130_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00135_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00139_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00129_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00154_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00157_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00158_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00160_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00142_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00163_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00164_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00165_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00161_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00169_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00170_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00171_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00092_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00174_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00175_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00176_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00167_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN00015_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN00790_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN00853_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AG00172_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN00932_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN00965_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN01039_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN01044_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN00010_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN01084_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN01173_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN01174_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN01184_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN00914_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN01218_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN01251_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN01545_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN01216_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN02724_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN03500_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN02122_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04117_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04134_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN01060_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04191_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04195_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04196_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN02559_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04225_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04235_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04267_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04108_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04323_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04326_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04332_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04355_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04369_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04269_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04385_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD00116_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD00141_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04206_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD00155_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD00160_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD00173_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD05119_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04174_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD06200_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD07761_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD07804_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\AN04384_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD07831_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD08758_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD08773_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD00146_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD08868_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD09031_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD06102_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD09662_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD10890_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD10972_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD09194_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD19563_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD09664_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD19695_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD19827_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD19828_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD08808_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD19988_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD20013_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00012_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00045_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00098_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00105_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD19582_.GIF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00008_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00130_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00148_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00152_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00194_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00195_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00234_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BD19986_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00247_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00248_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00252_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00254_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00122_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00262_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00265_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00267_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Logs\Setup.evtx.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00270_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00273_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00274_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00242_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00390_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00392_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00261_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00525_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00526_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00648_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00269_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00923_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00932_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00985_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Logs\Security.evtx.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00296_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BOATINST.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00076_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00078_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00524_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00100_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00135_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00136_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BL00921_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00174_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00184_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00186_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BOAT.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00224_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00438_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00439_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Logs\System.evtx.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00092_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00441_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00442_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00145_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00444_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00445_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00200_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS01080_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS01603_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS01634_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00440_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Common Files\DESIGNER\MSADDNDR.OLB.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Common Files\microsoft shared\ClickToRun\AppvIsvStream32.dll.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS01635_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS01637_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS01638_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS01639_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS01636_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\CLASSIC1.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\CLASSIC2.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\CLIP.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00443_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\CRANINST.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\CUP.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\CUPINST.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\BS00453_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\DD00121_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\DD00234_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\DD00255_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\CG1606.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\DD00261_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
-
Rule "DharmaEncryptedFile" from ruleset "Ransomware" has matched on the dropped file "C:\Program Files\Microsoft Office\root\CLIPART\PUB60COR\DD00297_.WMF.id-B4197730.[seavays@aol.com].save".
|
|
|
4/5
|
File System
|
Modifies content of user files
|
1
|
Ransomware
|
|
|
-
Modifies the content of multiple user files. This is an indicator for an encryption attempt.
|
|
|
4/5
|
File System
|
Deletes user files
|
1
|
Wiper
|
|
|
-
Deletes multiple user files. This is an indicator for ransomware or wiper malware.
|
|
|
4/5
|
OS
|
Modifies Windows automatic backups
|
1
|
-
|
|
|
-
Deletes Windows volume shadow copies.
|
|
|
2/5
|
Anti Analysis
|
Resolves APIs dynamically to possibly evade static detection
|
1
|
-
|
|
|
-
Resolves an unusually high number of APIs.
|
|
|
2/5
|
Anti Analysis
|
Tries to detect virtual machine
|
1
|
-
|
|
|
-
Possibly trying to detect VM via rdtsc.
|
|
|
1/5
|
Process
|
Creates system object
|
2
|
-
|
|
|
-
Creates mutex with name "Global\syncronize_8B9U41A".
|
|
|
-
Creates mutex with name "Global\syncronize_8B9U41U".
|
|
|
1/5
|
File System
|
Modifies operating system directory
|
1
|
-
|
|
|
-
Creates file "C:\WINDOWS\System32\wmxsde.exe" in the OS directory.
|
|
|
1/5
|
Persistence
|
Installs system startup script or application
|
5
|
-
|
|
|
-
Adds "C:\WINDOWS\System32\wmxsde.exe" to Windows startup via registry.
|
|
|
-
Adds "c:\users\fd1hvy\appdata\roaming\microsoft\windows\start menu\programs\startup\wmxsde.exe" to Windows startup folder.
|
|
|
-
Adds "c:\programdata\microsoft\windows\start menu\programs\startup\wmxsde.exe" to Windows startup folder.
|
|
|
-
Adds "7686488" to Windows startup via registry.
|
|
|
-
Adds "C:\Users\FD1HVy\AppData\Roaming\wmxsde.exe" to Windows startup via registry.
|
|
|
1/5
|
Process
|
Creates process with hidden window
|
1
|
-
|
|
|
-
The process "C:\WINDOWS\system32\cmd.exe" starts with hidden window.
|
|
|
1/5
|
Masquerade
|
Changes folder appearance
|
4
|
-
|
|
|
-
Folder "c:\$recycle.bin\s-1-5-18" has a changed appearance.
|
|
|
-
Folder "c:\$recycle.bin\s-1-5-21-1051304884-625712362-2192934891-1000" has a changed appearance.
|
|
|
-
Folder "c:\program files\common files\microsoft shared\stationery" has a changed appearance.
|
|
|
-
Folder "c:\program files" has a changed appearance.
|
|
|
1/5
|
File System
|
Modifies application directory
|
1433
|
-
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\c2rheartbeatconfig.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\officeupdateschedule.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\servicewatcherschedule.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\stationery\desktop.ini.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\desktop.ini.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\server\xusage.txt.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\ffjcext.zip.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\splash.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\splash_11-lic.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\splash_11@2x-lic.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\images\cursors\invalid32x32.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\images\cursors\win32_copynodrop32x32.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\images\cursors\win32_linkdrop32x32.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\images\cursors\win32_linknodrop32x32.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\images\cursors\win32_movedrop32x32.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\images\cursors\win32_copydrop32x32.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\jvm.hprof.txt.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\tzdb.dat.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\thirdpartylicensereadme-javafx.txt.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\thirdpartylicensereadme.txt.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\splash@2x.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\images\cursors\win32_movenodrop32x32.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\filesystemmetadata.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\readme.txt.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\office16\ospp.htm.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\office16\slerror.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0015-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\welcome.html.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0015-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0016-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\appxmanifest.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\office16\ospp.vbs.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0016-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0018-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0018-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0019-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0019-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-001a-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-001a-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-001b-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-001f-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-001b-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-001f-040c-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-001f-0c0a-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0027-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-002c-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0054-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-006e-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0090-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0090-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-00a1-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0057-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-00ba-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-00ba-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-00c1-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-00a1-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-00c1-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-00e1-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-00e1-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-00e2-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0115-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-0117-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-00b4-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-012b-0409-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-3101-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifestloc.en-us.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\authoredextensions.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-00e2-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00011_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00021_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00037_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00004_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00040_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00052_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00057_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.90160000-012a-0000-1000-0000000ff1ce.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\packagemanifests\appxmanifest.common.xml.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00038_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00090_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00103_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00120_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00126_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00130_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00135_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00139_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00142_.gif".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00129_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00154_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00157_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00158_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00160_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00142_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00163_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00164_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00165_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00161_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00169_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00170_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00171_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00092_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00174_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00175_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00176_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00167_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an00015_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an00790_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an00853_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ag00172_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an00932_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an00965_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an01039_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an01044_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an00010_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an01084_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an01173_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an01174_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an01184_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an00914_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an01218_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an01251_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an01545_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an01216_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an02724_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an03500_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an02122_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04117_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04134_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an01060_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04191_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04195_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04196_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an02559_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04225_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04235_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04267_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04108_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04323_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04326_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04332_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04174_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04206_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04269_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04355_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04369_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04385_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd00116_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd00141_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd00155_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd00160_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd00173_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd05119_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd06200_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd07761_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd07804_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\an04384_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd07831_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd08758_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd08773_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd00146_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd08868_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd09031_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd08808_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd09662_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd10890_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd10972_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd09194_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd19563_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd09664_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd19695_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd19827_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd19828_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd19988_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd20013_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00012_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00045_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00098_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00105_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd19582_.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bd19986_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00008_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00130_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00148_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00152_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00194_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00195_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00234_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00247_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00248_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00252_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00254_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00122_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00262_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00265_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00267_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00270_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00273_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00274_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00242_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00390_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00392_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00261_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00525_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00526_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00648_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00269_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00923_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00932_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00985_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00296_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\boatinst.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00076_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00078_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00524_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00100_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00135_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00136_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bl00921_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00174_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00184_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00186_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\boat.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00224_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00438_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00439_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-core-file-l1-2-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-core-localization-l1-2-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-core-processthreads-l1-1-1.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-core-file-l2-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-core-timezone-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-core-xstate-l2-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00092_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00441_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00442_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00145_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00444_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00445_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00200_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs01080_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs01603_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs01634_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00440_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\designer\msaddndr.olb.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-convert-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-core-synch-l1-2-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-conio-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-locale-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00443_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs00453_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-environment-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-multibyte-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-private-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-math-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-runtime-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-stdio-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-string-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-heap-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-time-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-utility-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-filesystem-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\appvisvstream32.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs01635_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs01637_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs01638_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs01639_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\bs01636_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\classic1.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\classic2.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\clip.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\crane.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\craninst.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\cup.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\cupinst.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00121_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00234_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\api-ms-win-crt-process-l1-1-0.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00255_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\appvscripting.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\appvcleaner.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\appvshnotify.exe".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00261_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00297_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00117_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00256_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\appvisvsubsystems32.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\appvshnotify.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\c2r32.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\c2rui.en-us.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\i640.hash.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\i641033.hash.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\mavinject32.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00407_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00413_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00414_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00419_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00372_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00448_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00449_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00687_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00705_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00405_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01138_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01139_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01140_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01039_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01145_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01146_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01151_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01015_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01157_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01160_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\concrt140.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\integratedoffice.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd00437_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01163_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01166_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01167_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01168_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01143_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01170_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01171_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01172_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01152_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01162_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01169_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01176_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01178_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01179_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01181_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01182_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01183_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01186_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01173_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01434_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01585_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01586_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01628_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01180_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01631_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01761_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01772_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01793_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ed00010_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\dd01630_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ed00172_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ed00184_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\en00006_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\en00202_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ed00019_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\officec2rclient.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\officec2rcom.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\msointl30.en-us.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\ucrtbase.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\clicktorun\vccorlib140.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\ink\en-us\flicklearningwizard.exe.mui".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\en00222_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\en00242_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\en00319_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\en00397_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\en00902_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00074_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00077_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00086_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00090_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\office16\liclua.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\office16\office setup controller\pkeyconfig.companion.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\source engine\ose.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\en00320_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00076_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\office16\office setup controller\pkeyconfig-office.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\office16\office setup controller\pidgenx.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\vc\msdia100.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\vc\msdia90.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00096_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00297_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00306_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00336_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00361_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00296_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00382_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00397_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00403_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00414_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00428_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00435_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00438_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00455_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00543_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00544_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00564_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00586_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\vsto\10.0\1033\vstoinstallerui.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\vsto\10.0\1033\vstoloaderui.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\vsto\10.0\vstoinstaller.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00369_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00419_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00459_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\vsto\10.0\vstoloader.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00779_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00799_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00814_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd01074_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd01084_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd01176_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\vsto\vstoee.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\vsto\vstoee100.tlb.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\vsto\vstoee90.tlb.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd01193_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd01196_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd01548_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00775_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd01658_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd01659_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\microsoft shared\vsto\10.0\vstomessageprovider.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\internet explorer\signup\install.ins.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\awt.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\bci.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\dcpr.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\decora_sse.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\dtplugin\deployjava1.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd00965_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd02068_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd02071_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd01191_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd02088_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd02097_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd02115_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd01657_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd02141_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd02153_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd02158_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd01660_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\flap.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00057_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00084_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00231_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\dtplugin\npdeployjava1.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\deploy.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd02075_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00236_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00241_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd02116_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00276_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00334_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00443_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fd02161_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00524_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00526_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00527_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00546_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00235_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00602_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00612_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00623_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\fontmanager.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\fxplugins.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\dt_socket.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\glass.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\eula.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\dt_shmem.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\gstreamer-lite.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00260_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00625_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00636_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00669_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00513_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00685_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00687_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00688_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00693_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00601_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\hprof.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\instrument.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\j2pcsc.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\glib-lite.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jaas_nt.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jabswitch.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\java.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\java.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\javacpl.cpl.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\javacpl.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\javafx_font.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh00681_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\j2pkcs11.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\javafx_iio.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\javaw.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\java-rmi.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\java_crw_demo.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jawt.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jawtaccessbridge-64.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\javaaccessbridge-64.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\javafx_font_t2k.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh01013_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh01058_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh01065_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh01080_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh01242_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh01015_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh01329_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh01461_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh01618_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh01875_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh01923_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh02155_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh02282_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh02298_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh02312_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\javaws.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh01291_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh02313_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hm00005_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hm00114_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh01759_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hm00172_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hm00426_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\in00046_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hh02166_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\hm00116_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jdwp.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jfxmedia.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\in00177_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\in00204_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jjs.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\in00233_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\in00343_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jfr.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jp2iexp.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\in00557_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\in00915_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\in00919_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\in00956_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\in00957_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0075478.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0086384.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0086420.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jfxwebkit.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jli.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\in00346_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\in00351_.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jp2native.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jp2ssv.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0086424.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0086428.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0086432.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0086478.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0086426.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0089992.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0090027.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0090087.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0090149.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0090390.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0090777.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0090781.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0090783.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0093905.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jpeg.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jsound.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jsoundds.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jp2launcher.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\keytool.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\kinit.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\klist.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\jsdt.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\lcms.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\management.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\mlib_image.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\ktab.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\msvcr100.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0089945.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099145.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099146.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099147.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0090089.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099149.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099150.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099151.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0090779.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099153.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099154.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099155.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0098497.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099157.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099158.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099159.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\kcms.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\net.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\nio.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\npt.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\msvcp120.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099148.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099160.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099161.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099152.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099163.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099164.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099165.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099156.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099167.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099168.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099170.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099171.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\msvcr120.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\orbd.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\plugin2\npjp2.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\policytool.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\pack200.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\prism_common.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\prism_d3d.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\plugin2\msvcr100.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099162.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099173.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099174.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099175.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099166.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099177.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099178.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099169.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099172.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\rmid.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\rmiregistry.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\server\jvm.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\prism_sw.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\servertool.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\splashscreen.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\resource.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\ssvagent.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\sunec.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099176.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\server\classes.jsa.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\copyright.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\accessibility.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\calendars.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\classlist.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\cmm\ciexyz.pf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\amd64\jvm.cfg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\cmm\linear_rgb.pf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\cmm\srgb.pf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\content-types.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\cmm\gray.pf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\cmm\pycc.pf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\currency.data.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099179.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099181.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099182.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\messages_es.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\messages_fr.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099180.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099185.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099187.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099183.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099189.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099190.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\messages.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\messages_ja.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\messages_pt_br.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\messages_sv.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\messages_de.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\messages_zh_cn.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\messages_it.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099184.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099192.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099186.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099191.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\messages_zh_hk.properties".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\ext\access-bridge-64.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\messages_zh_hk.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\ext\dnsns.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099194.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\ext\jaccess.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099195.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099196.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099197.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099198.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\messages_zh_tw.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\ext\sunec.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\ext\sunmscapi.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\ext\sunpkcs11.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\ext\zipfs.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\flavormap.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\ext\meta-index.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\fontconfig.bfc.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\fontconfig.properties.src.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\ext\sunjce_provider.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\fonts\lucidabrightdemibold.ttf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\fonts\lucidabrightdemiitalic.ttf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099188.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099200.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099201.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099202.gif".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099202.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099203.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\fonts\lucidabrightitalic.ttf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\fonts\lucidatypewriterbold.ttf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\fonts\lucidabrightregular.ttf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099205.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0101856.bmp.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099204.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0101858.bmp".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0101859.bmp.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0101857.bmp.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0101860.bmp.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0101861.bmp.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0101858.bmp.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0101862.bmp.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0101863.bmp.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0101865.bmp.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0101866.bmp.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\fonts\lucidasansregular.ttf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0101867.bmp.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0102002.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0102594.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0102984.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0103058.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0101980.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0103402.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0101864.bmp.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0103850.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0103262.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0103812.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105232.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\fonts\lucidatypewriterregular.ttf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105238.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105240.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0102762.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105246.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105234.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105266.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105272.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105280.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105250.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105286.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105276.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105292.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105294.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105282.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105288.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105306.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105328.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105298.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105332.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\javafx.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\jce.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\javaws.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105336.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\images\cursors\cursors.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\jfr\default.jfc.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\jfr\profile.jfc.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\hijrah-config-umalqura.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\jfr.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105338.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105348.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\jfxswt.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105368.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105376.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\logging.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\management\jmxremote.access.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105360.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\jsse.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105380.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105384.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\management\jmxremote.password.template".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105388.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105390.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105378.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105320.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105396.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105410.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\management\jmxremote.password.template.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\management\management.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105414.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105490.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105386.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105502.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105398.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105506.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105520.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105412.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105530.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105588.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\management\snmp.acl.template.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\net.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\psfont.properties.ja.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\management-agent.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\security\blacklist.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105496.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105600.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\meta-index".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105526.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\psfontj2d.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\security\blacklisted.certs.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105912.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\security\cacerts.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\security\java.policy".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105974.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0106020.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0106124.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0106146.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0106208.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0106208.wmf".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\security\javaws.policy.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\security\java.security.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\security\us_export_policy.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0106222.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0106958.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107024.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\security\java.policy.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\sound.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\security\local_policy.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\tzmappings.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\license.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107026.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107042.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107090.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107130.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\release.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107132.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107134.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107138.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107146.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107148.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0106572.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107152.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107158.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107182.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107154.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107150.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107188.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107192.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107254.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107262.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107264.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\carbn_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\cmnty_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fall_01.mid".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107266.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\east_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fincl_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107266.wmf".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107280.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\explr_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\grden_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\grid_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fall_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\indst_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\java_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107288.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107290.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\fincl_02.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107282.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\htech_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107302.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107308.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\music_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\nbook_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\outdr_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\paper_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107314.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107316.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107342.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107344.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107358.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107364.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\ocean_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\parnt_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107426.wmf".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107450.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107452.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107426.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107456.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\parnt_02.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\parnt_03.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\parnt_04.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107458.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107480.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107482.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107328.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107488.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107490.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107484.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\parnt_06.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\parnt_08.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\parnt_09.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\parnt_07.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\road_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\jngle_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\schol_02.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\parnt_05.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\space_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\parnt_10.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\safri_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\show_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107492.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107496.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107500.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107468.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107512.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107514.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107502.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107494.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107526.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\sprng_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107446.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107544.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107516.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107708.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107712.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107528.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\swest_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107658.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107718.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107722.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\urban_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\vctrn_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107724.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107728.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\wnter_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\document themes 16\theme effects\banded edge.eftx.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\sumer_01.mid.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\document themes 16\theme effects\extreme shadow.eftx.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\document themes 16\theme effects\frosted glass.eftx.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107742.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107744.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\document themes 16\theme effects\glossy.eftx.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107746.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107748.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107734.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107750.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0107730.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0144773.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0136865.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0145168.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\document themes 16\theme effects\glow edge.eftx.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\document themes 16\theme effects\inset.eftx.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\document themes 16\theme effects\grunge texture.eftx.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0145272.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0145361.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0145373.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0145669.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\document themes 16\theme effects\milk glass.eftx.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\document themes 16\theme effects\office 2007 - 2010.eftx.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\document themes 16\theme effects\reflection.eftx.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\document themes 16\theme effects\smokey glass.eftx.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0145810.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\document themes 16\theme effects\top shadow.eftx.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\document themes 16\theme effects\riblet.eftx.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\document themes 16\theme effects\subtle solids.eftx.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0145707.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0145879.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0145895.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0145904.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0146142.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0148757.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0145212.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0149018.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\flattener\appvpackaging.dll.manifest.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0150150.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0148309.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0151041.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\flattener\appvopcservices.dll.manifest.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\integration\windows6.1-kb2999226-x86.msu.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0150861.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0148798.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\integration\windows6.1-kb2999226-x64.msu.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\integration\windows8-rt-kb2999226-x64.msu.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\integration\windows8-rt-kb2999226-x86.msu.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\integration\windows8.1-kb2999226-x64.msu.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0151045.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0151055.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0151061.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0151063.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0151067.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0151073.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0151581.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\integration\windows8.1-kb2999226-x86.msu.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152430.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessr_oem_perp-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152432.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152436.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152556.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152558.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessr_oem_perp-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessr_oem_perp-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152560.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessr_oem_perp-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessr_retail-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessr_retail-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessr_retail-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessr_retail-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessr_trial-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessr_trial-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessvl_kms_client-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessvl_kms_client-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessvl_kms_client-ul.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessvl_mak-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessvl_mak-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessr_trial-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessvl_mak-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\client-issuance-bridge-office.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\client-issuance-root-bridge-test.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\client-issuance-stil.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\client-issuance-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\client-issuance-ul.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelr_grace-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\accessvl_mak-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelr_grace-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\client-issuance-root.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelr_oem_perp-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelr_oem_perp-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelr_oem_perp-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelr_retail-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152568.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152600.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152590.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152602.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelr_retail-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelr_retail-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelr_trial-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelr_trial-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelr_oem_perp-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelvl_kms_client-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelvl_kms_client-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelr_trial-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelvl_kms_client-ul.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelvl_mak-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelvl_mak-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelvl_mak-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessdemor_bypasstrial180-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152606.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152610.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152622.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessdemor_bypasstrial180-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinesspipcr_grace-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\excelvl_mak-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinesspipcr_grace-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinesspipcr_oem_perp-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessdemor_bypasstrial180-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinesspipcr_oem_perp-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152626.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152628.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinesspipcr_oem_perp-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinesspipcr_oem_perp-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_grace-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152570.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152688.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152690.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152608.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152694.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152594.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152698.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152704.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152708.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152716.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_grace-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp2-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp2-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp2-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp2-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp3-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp3-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp3-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152696.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152722.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152878.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152882.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152702.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152884.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152876.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152892.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152898.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153047.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0152890.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153087.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153089.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153091.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153095.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153265.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153265.wmf".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153299.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153093.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153305.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153273.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153313.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153398.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153508.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153307.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153307.wmf".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153516.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0156537.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0157167.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153514.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0157191.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0157831.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0158071.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0158477.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp4-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp4-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0153518.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0160590.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0168644.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0171847.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0172035.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0172193.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0174315.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp3-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_retail-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_retail-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0164153.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0174639.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0171685.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0172067.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0175428.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0174635.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0174952.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0177806.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0177806.jpg".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_retail-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0175361.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0178348.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0177257.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0178460.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_retail-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0178523.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0178932.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0178632.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0179963.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_oem_perp4-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0178459.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0182689.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0178639.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0182888.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0182898.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0182946.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0183172.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0183174.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0183198.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0183574.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0182902.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0185670.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_retail2-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_retail3-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_retail2-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_retail3-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_retail3-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_retail2-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_retail3-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_trial-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_trial-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_retail2-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_trial-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0185778.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0185780.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_trial2-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_trial2-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentdemor_bypasstrial180-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentdemor_bypasstrial180-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentdemor_bypasstrial180-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_grace-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_grace-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_oem_perp-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homebusinessr_trial2-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_oem_perp-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_oem_perp-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_retail-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0185786.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0185790.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_oem_perp-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_retail-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_retail-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_trial-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0185796.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_retail-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0185798.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0185806.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_trial-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_trial2-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_trial2-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_trial2-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0185818.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0185828.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\homestudentr_trial-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0185800.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0185834.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_bypasstrial180-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0185842.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0186360.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_grace-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_grace-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_bypasstrial180-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_kms_automation-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_bypasstrial180-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_kms_automation-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_oem_perp-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_oem_perp-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0186362.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187647.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187815.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_kms_automation-ul.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0186364.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187825.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_oem_perp-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_retail-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187819.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187829.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187817.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187835.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0186346.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187837.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187839.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187847.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_oem_perp-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_retail-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_retail-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subscription-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187859.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187861.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187851.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187881.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187883.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187863.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187849.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187895.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187921.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0188511.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subscription2-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subscription2-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0187893.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0188519.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subscription-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subtest-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subscription-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subtest-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_retail-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subtest2-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0188513.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subscription2-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0188667.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0188679.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subtest-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subtest2-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0195248.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0195260.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0195254.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0195320.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subtrial-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subtrial-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subtrial-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subtrial2-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subtest2-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subtrial2-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_trial-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_trial-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0188587.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0195428.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0188669.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0195788.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_subtrial2-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondor_trial-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondovl_kms_client-ul.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondovl_kms_client-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondovl_mak-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondovl_mak-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondovl_mak-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondovl_mak-ul-phn.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365businessr_grace-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0196060.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0196142.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0196110.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0196358.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0195342.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0197979.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365businessr_grace-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0196364.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365businessr_subscription-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365businessr_subscription-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365businessr_subtest-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\mondovl_kms_client-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365businessr_subtest-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365businessr_subscription-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365businessr_subtrial-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365businessr_subtrial-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremdemor_bypasstrial180-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365businessr_subtest-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremdemor_bypasstrial180-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_grace-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0197983.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0198016.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription1-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription1-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365businessr_subtrial-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription2-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription2-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremdemor_bypasstrial180-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_grace-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription1-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0195772.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0198020.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0196354.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0198022.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0198025.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0198102.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0198021.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0198113.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0198226.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0198234.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription2-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription3-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription4-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription4-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription3-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription3-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription4-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription5-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription5-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest1-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest1-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest2-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0198377.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest2-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest3-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subscription5-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest3-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest1-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest4-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest4-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest2-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest4-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0198447.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0198712.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0198372.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0199303.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest5-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest5-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial1-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0198494.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0199423.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial1-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial2-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest5-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial2-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0199279.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0199465.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0199469.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0199307.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtest3-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial1-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial3-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0199429.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial4-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial2-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0199473.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0199475.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0200151.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0200163.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial3-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial3-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial4-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial4-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial5-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial5-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365proplusdemor_bypasstrial180-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365proplusdemor_bypasstrial180-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365proplusr_grace-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365proplusr_subscription1-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0200189.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0200273.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0199609.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0200183.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365homepremr_subtrial5-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365proplusdemor_bypasstrial180-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365proplusr_grace-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0199483.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0200279.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0200467.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0200383.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0200611.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0202045.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0200377.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0211981.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0212299.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0200289.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0212601.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0212685.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0200521.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0212953.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0213243.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0212751.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0214934.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0213449.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0214948.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0215076.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0215210.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365proplusr_subscription1-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365proplusr_subscription2-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0215070.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0215718.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0216112.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365proplusr_subscription3-pl.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365proplusr_subscription3-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0215709.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365proplusr_subscription1-ul-oob.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0215710.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0216153.jpg.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365proplusr_subscription3-ppd.xrm-ms".
|
|
|
-
Modifies "c:\program files\microsoft office\root\licenses16\o365proplusr_subscription2-ppd.xrm-ms.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\common files\scored-prices.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\internet explorer\determine keyboard rebecca.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\t2k.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099193.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0099199.gif.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\sunmscapi.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\ssv.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\unpack200.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\verify.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\wsdetect.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\tnameserv.exe.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\zip.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105230.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\w2k_lsa_auth.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\bin\windowsaccessbridge-64.dll.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105244.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\charsets.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy\messages_ko.properties.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105504.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\deploy.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\ext\cldrdata.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\ext\jfxrt.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\java\jre1.8.0_144\lib\ext\localedata.jar.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105638.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105710.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
-
Modifies "c:\program files\microsoft office\root\clipart\pub60cor\j0105846.wmf.id-b4197730.[seavays@aol.com].save".
|
|
|
1/5
|
Process
|
Reads from memory of another process
|
2
|
-
|
|
|
-
"c:\windows\system32\cmd.exe" reads from "C:\WINDOWS\system32\mode.com".
|
|
|
-
"c:\windows\system32\cmd.exe" reads from "C:\WINDOWS\system32\vssadmin.exe".
|
|
|
1/5
|
File System
|
Creates an unusually large number of files
|
1
|
-
|
|
|
-
Creates an unusually large number of files.
|
|
|
0/5
|
Process
|
Enumerates running processes
|
1
|
-
|
|
|
-
Enumerates running processes.
|
|
|