ZERO-FUCKS.exe
Created at 2019-07-15T02:10:00
VMRay Threat Indicators (7 rules, 13 matches)
| Severity | Category | Operation | Count | Classification | |
|---|---|---|---|---|---|
|
5/5
|
Local AV | Malicious content was detected by heuristic scan | 1 | - | |
|
|||||
|
4/5
|
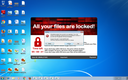
File System | Renames user files | 1 | Ransomware | |
|
|||||
|
4/5
|
File System | Modifies content of user files | 1 | Ransomware | |
|
|||||
|
1/5
|
Masquerade | Changes folder appearance | 7 | - | |
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
|||||
|
1/5
|
Device | Monitors mouse movements and clicks | 1 | - | |
|
|||||
|
1/5
|
File System | Creates an unusually large number of files | 1 | - | |
|
|||||
|
1/5
|
Static | Unparsable sections in file | 1 | - | |
|
|||||
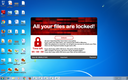
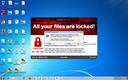
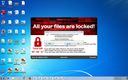
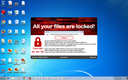
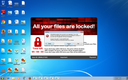
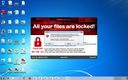
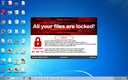
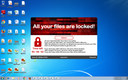
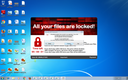
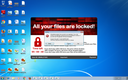
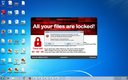
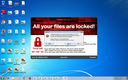
Screenshots
Monitored Processes
Sample Information
Analysis Information
| Creation Time | 2019-07-15 04:10 (UTC+2) |
| Analysis Duration | 00:02:42 |
| Number of Monitored Processes | 1 |
| Execution Successful |

|
| Reputation Enabled |

|
| WHOIS Enabled |

|
| Local AV Enabled |

|
| YARA Enabled |

|
| Number of AV Matches | 1 |
| Number of YARA Matches | 0 |
| Termination Reason | Maximum binlog size reached |
| Tags |